New: Flexible service plans for Myra WAF. Learn more!
Home>
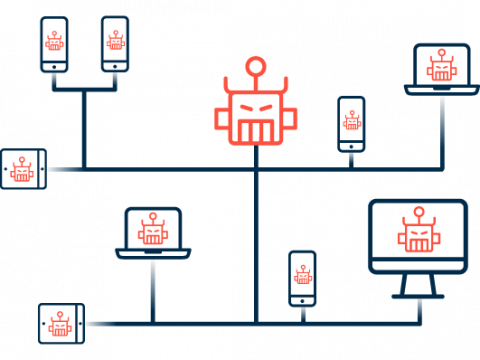
Botnet
03
How is a botnet formed?
A botnet is created in a number of stages:
1. Infection of unprotected computers
A computer can be infected in a number of ways, such as, for instance, via an infected website that has been infiltrated by malware. Infection via email also frequently occurs, either through attachments that contain malicious code or from links to an infected website. It also happens that users can install a completely different program that contains a Trojan. This is also how the door for the botnet is opened.
2. Integration into the botnet
The infected computers become part of an automated group of computers that spans the entire internet and joins together a large number of computers to form vast botnets. Most cybercriminals use botnets to carry out attacks over the internet. Attackers use what are called command-and-control (C&C) servers to control the bots. They are used for communication and data transmission to the individual bot programs on the network.
3. Use of botnets
There are legal applications of botnets, such as, for example, in data mining for cryptocurrencies. But botnets set up without the knowledge of computer users are used primarily for criminal purposes:
Distributed Denial of Service (DDoS) attacks
One of the types of attacks carried out by botnets are DDoS (Distributed Denial of Service) attacks in which the attackers aim to overload the resources of the target over the internet. Systems that are connected together through a bot network send countless meaningless requests to a specific web server until the server is brought to its knees by their sheer volume.
Spam
One of the most common uses of botnets is to send spam emails en masse.
Phishing
Botnets are also frequently used to surreptitiously send phishing emails from infected computers.
Data theft
Criminals can use botnets to gain access to sensitive user data, which they can either use themselves or sell to others.
Proxy
Proxies can be used to connect to a third computer via the infected computer. The actual source address is hidden.
Targeted advertising
The user of the infected computer may be shown special banner ads in their browser. These users may see offers for fake anti-spyware programs, among other things.
04
Known botnets
Certain botnets have gained notoriety over the years, often only after they have been broken up.
Mirai
Mirai is a type of Linux malware that primarily exploits vulnerabilities in everyday smart objects that are connected via the Internet of Things in order to insert malicious code. In 2016, the original botnet consisted of 500,000 compromised IoT devices around the world. The botnet eventually went on to infect a total of 3 million devices. Minecraft servers were attacked using the Mirai botnet between 2016 and 2018. The Dyn DNS service provider was also attacked in 2016. As a result, numerous large service providers went down for hours on end, including Twitter, Spotify, and Amazon.
Necurs
In March 2020, Microsoft managed to break up the Necurs botnet together with help from partners from 35 countries. The botnet consisted of more than 9 million infected computers and was considered one of the most active networks of its kind. Cybercriminals sometimes used Necurs to commit stock fraud as well as to send email spam and malware, such as the GameOver Zeus trojan. Microsoft developed scanning software specifically for Necurs so that it could check Windows PCs for the botnet.
Reaper
The Reaper botnet, discovered in 2017, is considered the successor to Mirai. This malware also primarily targeted smart home and other everyday devices. Reaper is estimated to have infected 10,000 to 20,000 IoT devices.
Avalanche
Avalanche was a global network that consisted of more than 20 combined botnets. At the end of 2016, the investigative authorities succeeded in breaking up Avalanche. The network was primarily used for phishing attacks: In 2009, it was supposedly responsible for two thirds of all attempted phishing attacks.
Bredolab
The Russian Bredolab botnet was mainly used to send spam emails with malware. This botnet was also broken up in 2010. At this point, we know that it consisted of millions of infected zombie computers.
Mariposa
Mariposa is one of the largest botnets discovered to date. A total of 13 million computers in 190 countries were infected by Mariposa, which was used primarily for data theft and was broken up in late 2009. The network had already collected data on 800,000 users, including access credentials for online banking and email accounts as well as corporate networks.
Dridex
Dridex disappeared from the scene in 2016, but before then was a botnet whose main purpose was to collect bank and credit card details. Windows users would become infected by opening email attachments that purported to be Word or Excel files. These files would install the Dridex malware on the user’s computer.
Echobot
Echobot is the latest successor to Mirai. It has been active since 2019. The distinctive feature of Echobot is that the botnet exploits the vulnerabilities of a variety of devices. This network cannot be put into a specific category. Rather, it attacks routers, cameras, and networking software, among other things.
06
What offers protection against botnets?
1. Protection of individual devices
The primary means for protecting computer systems from bot malware infection is to use the latest versions of software. Installing security updates for the operating system and other software soon after they are released reduces the potential attack surface of digital attacks. When using networked devices, it is also necessary to check whether an IP camera, scanner or other devices really need to be connected to the internet or whether access to a local network is enough. This reduces the likelihood that of becoming the target of attacks and makes it more complicated for your devices to be misused for malicious purposes.
2. Protection against DDoS attacks
If companies are attacked by botnets using DDoS attacks, they are only able to maintain the operation of their online and other network-based services using special DDoS protection services. DDoS protection solutions are available both as an appliance for use on premises and as a SECaaS service. The latter solution is not throttled by the available bandwidth of the company’s own connection and can therefore be used much more agilely. DDoS prevention uses special technologies to filter incoming traffic and thus differentiate between valid requests and malicious access attempts. Some companies that are particularly frequent targets of DDoS attacks leave their network security solutions permanently enabled, whereas others only use the solutions when necessary in order to save on costs.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.