New: Flexible service plans for Myra WAF. Learn more!
Home>
Application Security









![]init[](https://www.myrasecurity.com/assets/79302/1674209677-init_logo_farbe_190x74-1.png?auto=format)














Reliable Web Application Security Solutions
Advantages of Comprehensive Application Security
“Cyber incidents are the No. 1 business risk.” – Allianz Risk Barometer 2024

Protection against current and new threats
By implementing modern security solutions, companies can ensure that their applications are protected against the latest threats.

Secure access to web applications
By using technologies such as WAFs, access to web applications is secured without having to change them.

Fulfillment of compliance requirements
A robust security concept helps companies to comply with industry-specific regulations and avoid legal consequences.
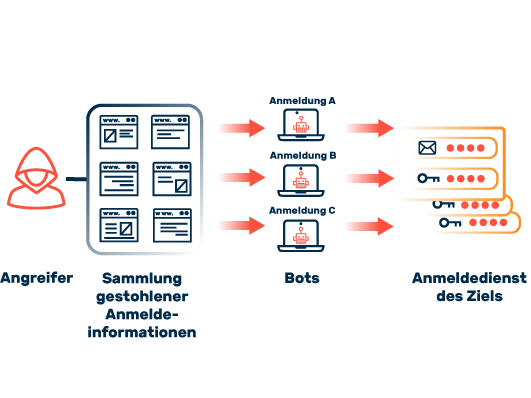
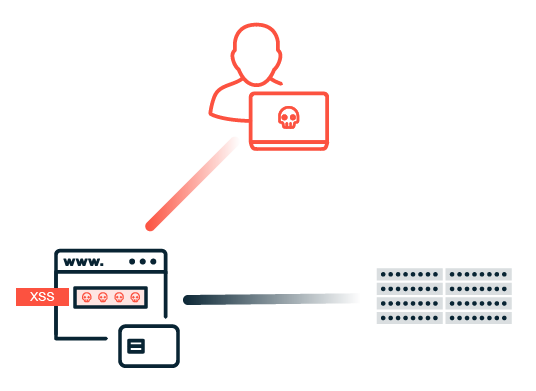
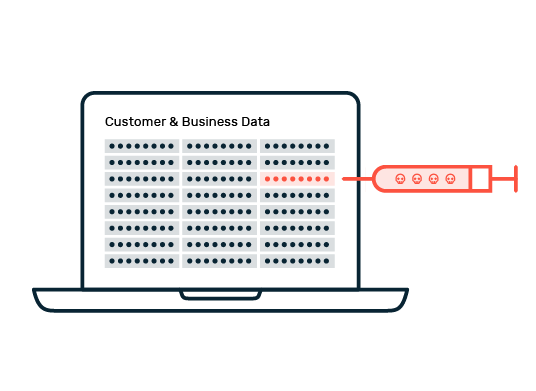
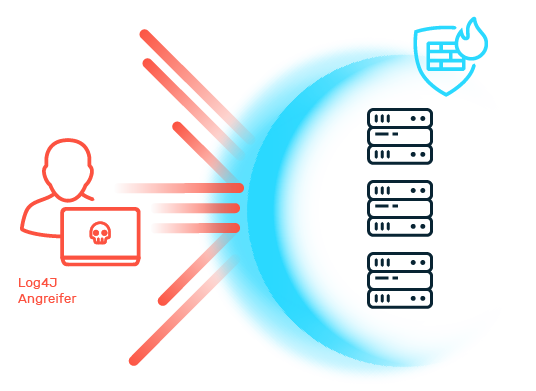
The Biggest Threats to Web Applications
Benefit from Industry-Recognized Expertise







Protect Your Web Applications With Myra
All features

Comprehensive Protection
Get protection against malicious requests, cross-site scripting, cross-site request forgery, SQL injection, OWASP Top 10 threats, and other critical dangers.
Flexible Load-Balancing Plans
Benefit from support for standard methods like Round Robin, IP Hash, or least connection, or go for self-defined and complex load balancing plans.

Name Resolution Protection
Rely on geo-redundant and hardened DNS servers with anycast routing and hidden primary functionalities for maximum protection and exceptional performance.
Geo-Redundant Performance and Stability
Accelerate content using either pull or push CDN functionalities.
Convenient Certificate Management
Issue automated SSL/TLS certificates and keep track of everything with a centralized management system.

Wide Range of Connectivity Options
Send clean traffic via Direct Connect, GRE tunnel, VLAN, or IPsec.

Detailed Monitoring
Constant ccess to real-time information on traffic and mitigation.
High-Definition Streaming
Get dynamic live stream delivery for optimal user experience, speed, and stability.

Granular Traffic Control
Enjoy targeted blocking, forwarding, allowlisting, or delaying requests with Myra.
Holistic Approach to Application Security
Application security refers to the measures and technologies developed to protect web applications from threats and vulnerabilities. As applications are increasingly operated online and process sensitive data, they are the focus of cyber attacks. Without suitable protection, attacks such as SQL injection, cross-site scripting (XSS) or DDoS attacks can have serious consequences for companies and users. Data leaks can result in confidential information falling into the hands of unauthorized persons.
This can lead to high financial losses and legal consequences. In addition, it can lead to business interruptions that impair business operations and cause lasting damage to customer confidence. A robust application security strategy is therefore essential to ensure the integrity, confidentiality and availability of your applications and at the same time strengthen the trust of your customers. Myra Security offers customized solutions that comprehensively meet these requirements.
Discover more of our Application Security Solutions
Application Load Balancer
Elevate user experience with low latency and optimized load balancing using Myra's Application Load Balancer. Distribute incoming requests effectively, balance the load across multiple backend servers, and achieve reduced response times. Keep your web applications running smoothly and efficiently.
Explore a World of Knowledge and Practical Insights in Our Resource Center! Browse our extensive collection of product sheets, fact sheets, white papers, and case studies to unlock the secrets of effective attack defense. Learn from real-world examples and find the best ways to protect your systems against threats.
Application Security – Frequently asked questions (FAQ)
Application security, often abbreviated as "AppSec", refers to the measures and practices put in place to protect software applications from security threats and vulnerabilities. It is a a critical aspect of cybersecurity, as many security breaches and data leaks occur through vulnerabillities in software applications. Web application security is a multifaceted field that involves a combination of technology, processes, and people to protect software applications from a wide range of threats, including unauthorized access, data breaches, and malware attacks.
Application security is crucial due to a number of different reasons: 1. Applications often handle sensitive user data, financial information, and confidential business data, making them prime targets for cyberattacks. 2. Security breaches can lead to severe reputational damage, eroding trust among customers and users. 3. Such incidents can result in substantial financial losses through theft, fraud, regulatory fines, and incident response costs. 4. Compliance requirements necessitate robust web application security to meet industry-specific regulations, preventing legal consequences and fines. 5. Application security is crucial for maintaining business continuity by reducing the risk of service interruptions caused by cyberattacks and vulnerabilities. In today's digital age, prioritizing web application security is not just a best practice; it's an essential component of responsible and sustainable business operations.
An application security provider specializes in safeguarding software applications from cybersecurity threats and vulnerabilities. They offer services such as security assessments, penetration testing, code review, and vulnerability remediation to identify and address weaknesses. These experts ensure that applications comply with industry regulations, provide training in secure coding practices, and implement robust incident response plans. Continuous monitoring and the deployment of security tools like Web Application Firewalls (WAFs) are also part of their repertoire.
The security of web applications (web application security) is a central aspect in the development and operation of cloud solutions. There are many different attack vectors to consider when securing web applications. The most common attack vectors to be addressed by web application security include: SQL injection, cross-site scripting (XSS), session hijacking, cross-site request forgery (CSRF), directory traversal, email injection, man-in-the-middle (MitM) attack, man-in-the-browser, distributed denial of service (DDoS). These and other risks must be addressed via protective measures from the Application Web Security area in order to ensure the confidentiality, integrity and availability of web resources.