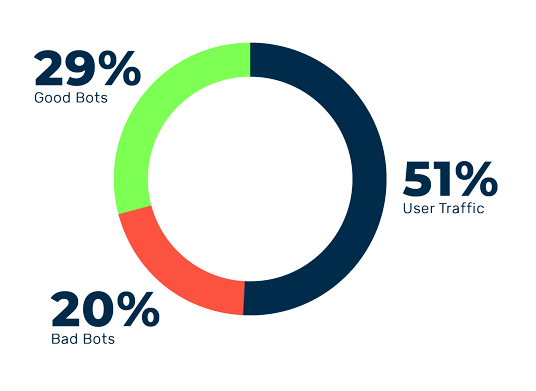New: Flexible service plans for Myra WAF. Learn more!
Take Control over Your Bot Traffic
This Is Why CISOs Choose Myra
Our key benefits at a glance

Unlock the Power of Our Comprehensive Certification
Experience peace of mind knowing that our cutting-edge technologies, exceptional services, and streamlined processes are meticulously audited and certified to exceed the highest industry standards.

Embrace Quality with Our "Made in Germany" Assurance
As a company based in Germany, we strictly adhere to the strict regulations imposed by the GDPR, ensuring that your data privacy is our top priority.

Experience Unmatched Support, Anytime, Anywhere!
Receive unparalleled assistance from a team of security experts, part of our reputable Myra Security Operations Center. We're available 24/7 to address any concerns and provide you with guidance.
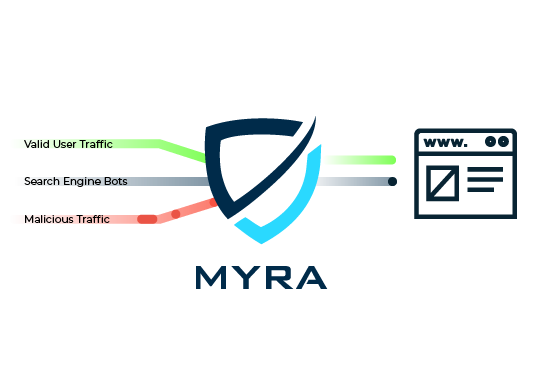
Protect Your Business from Malicious Bot Traffic
Myra Bot Manager reliably fends off automated threats.

Credential Stuffing
Bots can test masses of user/password-combinations in a very short time. Hits on active accounts are then sold or used for further attacks.

Web Scraping
Bots copy individual page contents or entire websites in a matter of seconds. Criminals use such a copy of the original page to steal credentials via phishing.

Click Fraud
Attackers use bots to automatically click on advertisements or affiliate links contained on websites in order to generate revenue at the advertisers' expense.

Account Creation & Takeover
Bots create a lot of fake user accounts or infiltrate existing accounts, which criminals then misuse for attacks or fraud attempts.

Form Spam
Bots bombard your company with messages via contact forms. This phishing method often serves criminals as a starting point for further attacks.

Skewing
Through bot-based queries, attackers deliberately manipulate web analytics data to trick you into making wrong strategic decisions and harm you.

Hype Sale Bots (Scalping)
Through automated bot requests, fraudsters secure coveted goods and then resell them at a high profit, negatively impacting your customer relationship.

Cart Abandonment / Inventory Hoarding
Bots fill shopping carts without completing the purchase process. This is detrimental to the business of your store, because regular customers can temporarily no longer buy the items.

Botnet-Based Overload Attacks
Via botnet, attackers send a flood of automated requests to your web server to overload it and cripple the pages or services hosted on it.









![]init[](https://www.myrasecurity.com/assets/79302/1674209677-init_logo_farbe_190x74-1.png?auto=format)














Myra Bot Management at a Glance
Key features

Passive Fingerprinting
Myra reliably detects any deployed bot software based on a unique fingerprint - independently of IP, ASN and User Agent.

Behavioral Analytics
Using behavioral analysis, Myra Bot Manager automatically identifies unusual request patterns.

Automation Tool Detection
Our bot detection reliably detects automation tools such as Selenium or PhantomJS.

Alternate Origin
If necessary, Myra redirects requests to alternative origin servers to protect the main infrastructure.

Fast and Easy Integration
Myra's cloud-based Bot Management Solution requires no additional hardware or software.

Flexible Control Options
Granular traffic control via Block, Allow, Browser Challenges (Javascript), Human User Challenges (Captcha), Log, Alert and Custom Challenges.
Protect Your Business Now:
Request an Offer
Discover Our Customized Offering!
Our comprehensive security solutions protect your business from the latest threats.
Get the solution that is perfectly tailored to your needs.
You can expect a response within 24 hours.
Our cloud approach means our products can be set up in no time.
Bot Manager – Frequently asked questions (FAQ)
A bot manager is a software that regulates access by bots to a website. The tool can distinguish human traffic from bot traffic and block unwanted access. Blocking all bot traffic is not advisable, as this would prevent useful bots such as search engine crawlers from accessing the site. Instead, clean bot management identifies trusted bots by recognizing the bot reputation, analyzing the originating IP addresses, and observing the bot's behavior. Trusted bots are added to an allowlist and can continue to access the website, while rogue and malicious bots are denied access.
Myra Deep Bot Management is a cloud-based service and as such is faster and easier to implement than comparable on-premises solutions. It requires no additional investment in hardware, software or skilled personnel. In addition, as a cloud solution, our Bot Manager is highly scalable. This is important in online retailing, for example, when more bot requests are expected on promotion days such as Black Friday.
Myra Deep Bot Management automatically detects bot software, automation tools and unusual access patterns using behavioral analysis and passive fingerprinting. For each page access, more than 50 attributes of the access are included in this fingerprint to uniquely identify the software used. As soon as the fingerprint is available, targeted measures can be taken or protective mechanisms activated. Unwanted and harmful accesses can be blocked, confronted with human interaction challenges (e.g. CAPTCHA) or otherwise controlled or redirected.