New: Flexible service plans for Myra WAF. Learn more!
Home>
Cyber warfare: US military succeeds in strike against the TrickBot botnet
Cyber warfare: US military succeeds in strike against the TrickBot botnet
SECURITY INSIGHTS | 2 November 2020
The operation carried out by the United States Cyber Command was apparently a pre-emptive strike to protect the U.S. presidential election. This example demonstrates the growing significance of cyber warfare in our increasingly interconnected world.


Cyber Command, the U.S. military agency entrusted with electronic warfare, has succeeded in massively disrupting the operation of the TrickBot botnet during a campaign lasting several weeks. The operation is considered part of the efforts to prevent the upcoming U.S. presidential election from being tampered with, according to the Washington Post.
Russian criminals are suspected to be behind TrickBot, one of the world’s largest botnets with at least one million hijacked computers. Originally, it was mainly used to steal credentials and spread banking Trojans. Over time, however, the people behind it have continued to develop the botnet, hiring it out for Distributed Denial of Service attacks (DDoS) and most recently using it for ransomware attacks. In ransomware attacks, attackers use embedded malware to encrypt massive amounts of data and demand payment of a large ransom for decrypting it.
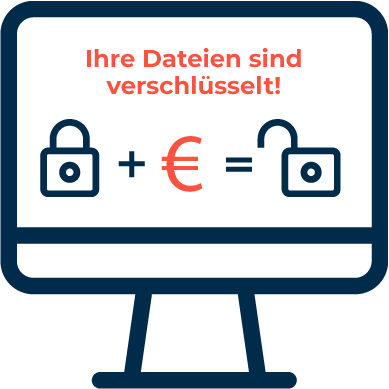
Ransomware as a possible disruptive factor in the U.S. presidential election
According to the Washington Post, U.S. Homeland Security fears that such ransomware attacks on state voter registration offices and related systems could massively disrupt preparations for the November 3 election or cause confusion and delays on election day itself. The pre-emptive strike against TrickBot by U.S. Cyber Command is unlikely to permanently shut down the botnet, U.S. officials told the newspaper.
Ransomware as a possible disruptive factor in the U.S. presidential election
According to the Washington Post, U.S. Homeland Security fears that such ransomware attacks on state voter registration offices and related systems could massively disrupt preparations for the November 3 election or cause confusion and delays on election day itself. The pre-emptive strike against TrickBot by U.S. Cyber Command is unlikely to permanently shut down the botnet, U.S. officials told the newspaper.

However, the botnet operators are likely to be distracted for at least a while and busy restoring normal conditions. This tactic of “imposing cumulative costs” on an opponent by keeping him constantly busy is a key element of U.S. Cyber Command’s strategy to protect the election from foreign threats.
Military intelligence agencies had already taken a similar approach in 2018 during the U.S. midterm elections. At that time, they sabotaged access to the internet for the Internet Research Agency, which was considered a Russian “troll factory,” in order to prevent influence from being exerted through targeted disinformation on the day of the election.
Cyber warfare gains significance
The actions taken by U.S. Cyber Command in these cases are an example of how governments are trying to defend themselves against cyber attacks from outside by going on the offensive themselves. Cyber warfare is becoming increasingly significant because information technology systems affect almost all areas of life—from telecommunications to transportation, trade, finance and health care, to energy and water supply. A disruption of these systems has far-reaching consequences for the entire country and its people.
Cyber warfare can be defined as the actions of a country or an international organization that attempt to attack and damage computers or information networks of another nation, by means of malware or Denial of Service (DoS) attacks, for example. As a rule, however, state-run cyber attacks are difficult to identify as such because countries almost never admit to them. Sometimes attacks are carried out by state-sponsored hacker groups that officially take responsibility for them, while their state sponsors deny any involvement. If no state institutions are involved, this is often referred to as cyber terrorism.
Cyber warfare can be defined as the actions of a country or an international organization that attempt to attack and damage computers or information networks of another nation, by means of malware or Denial of Service (DoS) attacks, for example. As a rule, however, state-run cyber attacks are difficult to identify as such because countries almost never admit to them. Sometimes attacks are carried out by state-sponsored hacker groups that officially take responsibility for them, while their state sponsors deny any involvement. If no state institutions are involved, this is often referred to as cyber terrorism.

An arms race without international rules poses a risk of escalation
Cyber warfare and cyber terrorism, along with data and identity theft and espionage, are cited as the greatest threats in the national cyber security strategies of 29 EU and NATO states, which Deloitte examined for its European Cyber Defense Report 2018. Among the most active players in cyber warfare are the U.S., Russia, and China, as well as hacker groups associated with these countries.
Countries are engaged in a veritable arms race. On the one hand, they want to use the benefits of cyber warfare for themselves— this is because cyber attacks can be at least as effective and efficient as conventional military operations, but do not put soldiers in harm’s way and are more difficult to trace, which in turn makes retaliation more difficult. On the other hand, state actors, for their part, fear the consequences of such attacks, which is why they are continually upgrading their cyber defense systems.
This ambivalence is probably the main reason why, unlike conventional warfare, no international set of rules for cyber warfare exists. As a result, cyber warfare remains a gray area. The combination of a continuous arms race and a lack of clear rules harbors the danger that conflicts escalate quickly and spiral out of control.

Cyber attacks have an enormous potential for damage
The main goal of cyber warfare is to disrupt information technology systems and networks in such a way that a country’s critical infrastructure, such as telecommunications, the finance system, as well as energy and water supply, collapses or only works to a limited extent. However, destabilization through targeted disinformation and propaganda can also be viewed as a goal of cyber warfare.
Cyber attacks have an enormous potential for damage
The main goal of cyber warfare is to disrupt information technology systems and networks in such a way that a country’s critical infrastructure, such as telecommunications, the finance system, as well as energy and water supply, collapses or only works to a limited extent. However, destabilization through targeted disinformation and propaganda can also be viewed as a goal of cyber warfare.

For example, fake news and hate campaigns on the internet can be a good way to incite the public to hate and distrust their own government. Other cyber warfare methods include prying on and stealing information, deleting or modifying content and data, and introducing compromised software or hardware that causes system failures.
The weapons of choice include phishing and social engineering campaigns to gain access to systems and information, malware such as viruses, worms, and Trojans to remotely control or sabotage systems, and ransomware to cripple systems temporarily or permanently. Botnet-based Distributed Denial of Service (DDoS) attacks play a key role. They are not only useful for specifically disrupting critical infrastructure, but can also be used to launch additional attacks or disguise them. A DDoS attack can be used to hit government or corporate networks with massive broadband attacks and then more easily infect overloaded systems with spyware or malware to steal or destroy data.
Examples from over two decades of cyber warfare
The first conflict in which cyber warfare played an important role was the Kosovo war in 1999, when NATO penetrated telephone networks and electronically infiltrated the systems of several banks in order to freeze the accounts of Serbian President Slobodan Milošević. In Estonia, a wave of DDoS attacks in 2007 crippled many national internet services. Affected were the websites of governmental and administrative agencies, banks, and the media, with the result that, among other things, online banking was no longer possible. Russia was presumed to be behind the attacks.

Examples from over two decades of cyber warfare
The first conflict in which cyber warfare played an important role was the Kosovo war in 1999, when NATO penetrated telephone networks and electronically infiltrated the systems of several banks in order to freeze the accounts of Serbian President Slobodan Milošević. In Estonia, a wave of DDoS attacks in 2007 crippled many national internet services. Affected were the websites of governmental and administrative agencies, banks, and the media, with the result that, among other things, online banking was no longer possible. Russia was presumed to be behind the attacks.

In 2010, the Stuxnet worm, presumably jointly developed by the U.S. and Israel to sabotage the Iranian nuclear program, hit the headlines. In 2015, the German Bundestag was the target of a massive hacker attack, which was later linked to the GRU, the Russian military secret service. Only recently the EU sanctioned several Russians implicated of being involved. In 2017, the NotPetya malware crippled millions of computers. The malware presumably developed by Russia to destroy data was mainly targeted at computers in Ukraine, but spread rapidly worldwide, causing hundreds of millions of dollars worth of damage. Only recently, six GRU hackers were accused by the U.S. of being responsible for these and other cyber attacks. The example of NotPetya shows how quickly cyber weapons can spiral out of control.
Nevertheless, no end to the arms race is in sight. Compared to conventional warfare, cyber warfare represents a cheap, simple, fast, and effective alternative. The weapons of war will become even more powerful in the future thanks to modern technologies such as artificial intelligence or quantum computing. And with increasing digitalization, the number of potential targets is increasing.
Myra protects critical infrastructure
Myra secures government websites and the online portals of government agencies such as bundeskanzlerin.de (German Chancellor’s website) and bundesgesundheitsministerium.de (German Federal Ministry of Health’s website). Our BSI-qualified [BSI = Federal Office for Information Security] Security-as-a-Service solutions also effectively protect web applications against overload attacks by political activists and cyber terrorists.
Related articles
Security Insights
20 October 2021
A scalpel, not a shotgun: DDoS extortion with increasing precision
Security Insights
05 April 2022
Hackers use Spring4Shell exploit for remote code execution
Myra News
05 May 2020