New: Flexible service plans for Myra WAF. Learn more!
Home>
Data Manipulation & Content Theft
What you need to know about Data Manipulation & Content Theft
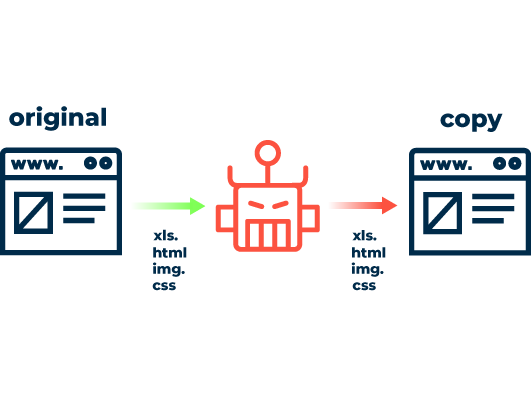
Digital crooks copy elaborately designed product pages, price structures and even entire shop structures for unscrupulous competitors. Cybercriminals also use digital duplicates for additional phishing attacks. Meanwhile, to sabotage companies, attackers use targeted bot requests to falsify the operators’ data analysis, provoking the wrong strategic decisions.
Technologically, the methods of fraud described are based on machine requests made by bots. Around 20 percent of average website traffic is accounted for by such requests. Against this background it is crucial for operators of online services to maintain full control over traffic at all times.