New: Flexible service plans for Myra WAF. Learn more!
Home>
DNS Attacks
What you need to know about DNS Attacks
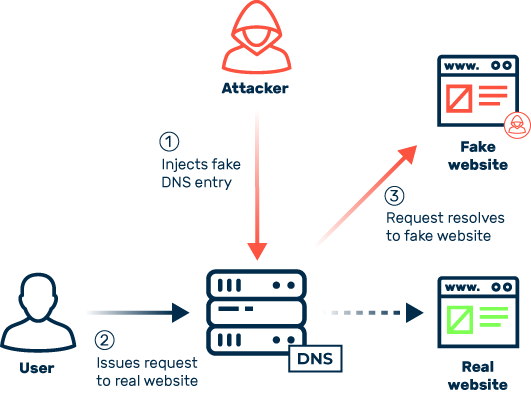
In cybersecurity, DNS attacks are defined as attacks that are either carried out via the Domain Name System (DNS) or that target the DNS directly. For example, cybercriminals can exploit key properties of the DNS to reinforce DDoS attacks. Other attack vectors such as DNS spoofing are designed to tamper with DNS entries in order to redirect internet users to specific websites.