New: Flexible service plans for Myra WAF. Learn more!
Home>
Factsheet: NIS-2 Compliance with Myra
Over 10 Years of Experience in Critical Infrastructure (KRITIS)
Myra Security has been protecting a wide range of organizations in sensitive and critical sectors for years, including healthcare services, financial institutions, insurance companies and government institutions. Thanks to its many years of experience and expertise, Myra knows the specific requirements and challenges associated with securing critical infrastructures.
Myra is itself a KRITIS company and therefore meets all compliance requirements.
Myra is an expert in protecting against cyber attacks in the KRITIS sector.
Our solutions are comprehensively certified and audited.






NIS-2 Timeline
The NIS-2 Directive was adopted by the European Parliament in November 2022 and came into force on January 16, 2023. From this date, the member states have 21 months to transpose the provisions into national law. This means that affected companies must fully implement the new regulations by October 17, 2024. The revised directive expands the scope and requirements of the original 2016 NIS Directive to reflect current threats and technological developments. In Germany, around 30,000 organizations are covered by the new regulation.


NIS-2-Compliant with Myra
in just 3 steps

Download the fact sheet
Find out which NIS 2 requirements we can support you with.

Identify need for action
In which areas do you not yet meet the NIS 2 requirements?

Get in touch
We help you with the implementation with our IT security solutions.
NIS-2-Compliance – Frequently asked questions (FAQ)
The NIS 2 Directive is an EU-wide regulation that aims to ensure a high level of cybersecurity across all member states. It extends the scope and requirements for operators of essential services and digital service providers. It includes stricter security measures, increased reporting obligations in the event of security incidents and increased cooperation between member states. It also places particular emphasis on risk management and securing critical infrastructure in order to strengthen resilience to cyber attacks.
Companies and organizations with at least 50 employees or an annual turnover of at least 10 million euros that belong to one of 18 defined sectors must comply with the directive.
KRITIS companies must be NIS-2 compliant by October 17, 2024. Therefore, affected companies must fulfill all relevant requirements by this date.
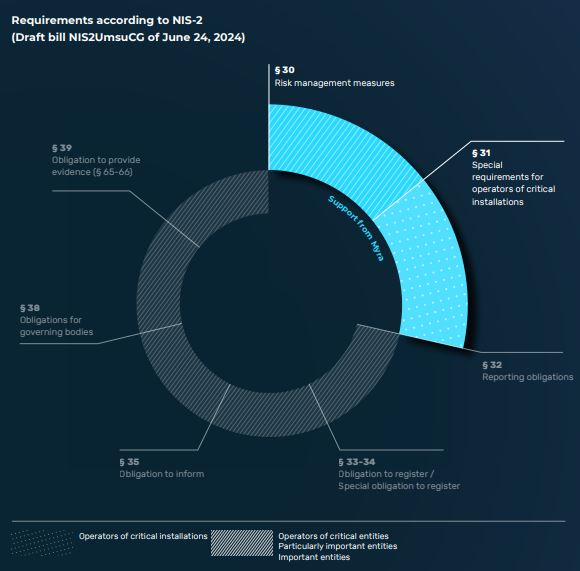
With its solutions for protection against cyber attacks at infrastructure and application level, Myra can make a decisive contribution to meeting compliance requirements, especially in the area of risk management (§ 30) and the special requirements for operators of critical facilities (§ 31). For the full list of requirements we support, simply download the fact sheet.