New: Flexible service plans for Myra WAF. Learn more!
Home>
Edge computing
At one look
- 1. A definition of edge computing
- 2. What are the advantages of edge computing?
- 3. How well does edge computing work in conjunction with the cloud, IoT, and 5G?
- 4. What are the vulnerabilities of edge computing?
- 5. What are the threats posed by edge computing?
- 6. What you need to know about edge computing
03
How well does edge computing work in conjunction with the cloud, IoT, and 5G?
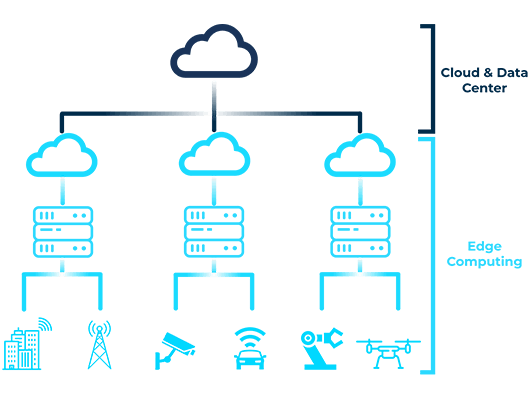
Edge computing is often misunderstood as a competitor or alternative to “traditional” cloud computing. In fact, both approaches work together in perfect harmony. The same can be seen with other popular technologies such as IoT (Internet of Things) or 5G mobile communications. In all of these areas, edge computing acts as a catalyst and enabler that enhances existing solutions or makes innovative approaches to solutions feasible in the first place.
Edge computing & cloud computing
Technological advances are allowing enterprises to shift more and more workloads to the network edge. This ensures low latency, which facilitates real-time applications, and lower bandwidth requirements. At the same time, edge computing also frees up resources and money in the cloud, where demanding big data calculations require maximum performance.
Edge computing & IoT
A combination of edge and cloud computing is also beneficial in IoT scenarios. In this case, data accumulating at the endpoints can be aggregated and processed locally. The already structured data sets are then transferred to the cloud for final processing. This approach also speeds up the overall process while at the same time reducing the requirements for bandwidth and computing power in the cloud.
Edge computing & 5G
In combination with the new 5G cellular standard, innovative solutions are also being found. This is where the speed advantages of edge computing meet low latency and high transfer rates in the cellular communications sector. With these properties, the technologies will enable high-precision traffic guidance systems that process traffic data in vehicles and on the road in real time and send it to the cloud for analysis using 5G.
04
What are the vulnerabilities of edge computing?
Compared to centralized topologies, where only a primary server system or a cloud data center needs to be secured, all endpoints involved in edge computing must be given equal attention in IT security. Depending on the type and scope of the edge network, this quickly results in a great deal of time and effort.
Secure hardware for the edge of the network
When selecting edge hardware, companies should limit themselves to the previously defined minimum requirements so as not to unnecessarily increase the network’s attack surface. For instance, is a USB slot on the device needed for operation, or would such an interface unnecessarily provide attackers access to the systems?
Using encryption to secure data
Simply due to local conditions, securing data at the network edge cannot hold a candle to the security standards of a data center. Data transmission between edge endpoints, gateways, and central control and cloud systems should be encrypted end-to-end. Even if attackers manage to infiltrate the system with a man-in-the-middle attack, data traffic is secure against eavesdropping and sabotage. Anyone who fails to use encryption protection risks expensive failures. Cybercriminals could, for example, tamper with the data sent by sensors in industrial plants to inflict serious damage on production equipment.
Protection from tampering is required
Edge systems must have a minimum level of protection against tampering to make it difficult for attackers to gain access to the network. This includes securely mounted housing covers and sensors that immediately report physical attempts of tampering. The issue of tamper-proofing is particularly important for devices that are installed in public spaces, where protection against access provided inside offices, production facilities, or factory halls is not available.
Lifecycle management
One-time setup and configuration of edge systems is not enough. With increasing requirements and new business processes, companies often have to adapt or expand their edge networks. In addition, the endpoints are not made to last forever and require maintenance and replacement when necessary. In order to avoid losing track of the network, detailed lifecycle management is required for deployment, decommissioning, onboarding to gateways and the cloud, and maintenance (software and hardware).
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.