New: Flexible service plans for Myra WAF. Learn more!
Home>
Encryption
At one
look
look
- 01. A definition of encryption
- 02. What data should be encrypted?
- 03. How is data encrypted?
- 04. Why is data encrypted?
- 05. What types of encryption are there?
- 06. What are the advantages and disadvantages of asymmetric and symmetric encryption?
- 07. What encryption standards are there?
- 08. Practical application scenarios
- 09. What you need to know about encryption
03
How is data encrypted?
Just as relevant as the type of data protected by encryption is the question of when to use encryption. The encrypted transfer of data on the internet has gained considerable momentum since Snowden’s revelations in 2013. Most commercial websites and internet services now use HTTPS encryption to secure communications. This common practice makes it difficult for attackers to capture data while in transit.
Encryption is also used to store data when it is not being actively used. This enables companies to protect their data from unauthorized access in a data center, for instance.
End-to-end encryption offers complete encryption over the entire communication path. This technology aims to ensure that only authorized senders and recipients are able to access the data. Even the provider of end-to-end encrypted services is unable to read the information arriving on its servers. For this reason, end-to-end encryption is particularly well suited for securing digital communications such as chats and emails.
05
What types of encryption are there?
In very basic terms, encryption methods can be divided into two categories: symmetric and asymmetric encryption. In practice, the two categories are not mutually exclusive per se. On the contrary, developers often use hybrid methods to combine the strengths of both methods.
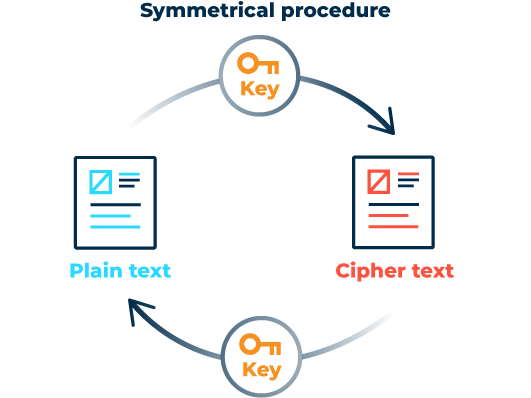
Symmetric methods
Here, encryption and decryption are performed using the same key. This means that both sender and receiver agree on and exchange the secret key before using it. A prominent example: The Caesar cipher, which the Roman commander bearing the same name is said to have used for his military correspondence, also uses only one cipher (key) and is therefore a symmetric method. For encryption, the letters of the alphabet are cyclically shifted to the right by a specific (secret) value. Decryption requires the opposite process by the same value.
While classic symmetric encryption methods work at the letter level to convert plaintext into encrypted text, ciphering in computer-aided cryptography methods takes place at the bit level. A distinction is made between stream ciphers and block ciphers.
Stream cipher
Each bit is associated with one bit of the keystream.
Block cipher
The bits being encrypted are grouped into blocks of fixed length and mapped to a fixed-length ciphertext.
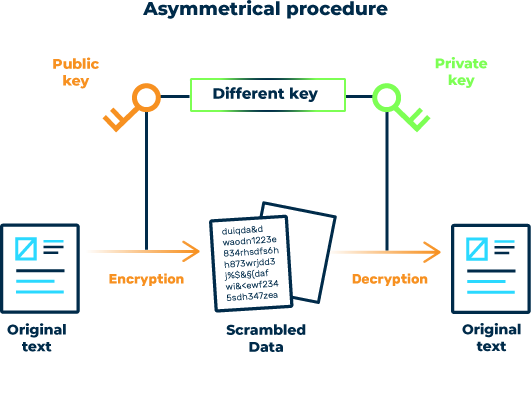
Asymmetric methods
These cryptographic methods use a pair of keys for each participant: a public key and a private key. While the public key, as its name suggests, is accessible to everyone, the private key remains secret. The sender uses the recipient’s public key for encryption, while the recipient uses his private key for decryption. The asymmetry results from the fact that data encrypted with the public key can only be decrypted with the secret private key of the key pair. RSA is the most well-known asymmetric method.
Hybrid methods
The data itself is encrypted using a symmetrical procedure. However, to increase security, an asymmetric procedure is used for the key exchange.
06
What are the advantages and disadvantages of asymmetric and symmetric encryption?
Of course, there are advantages and disadvantages to the various encryption methods – so it is important to carefully evaluate which encryption best meets the specific security requirement.
07
What encryption standards are there?
A number of years have gone by since the first cryptography methods were introduced—encryption options today are characterized by high-tech. Here are some of the most important solutions that definitively need to be mentioned in this context:
Data Encryption Standard (DES)
The widely used symmetric-key algorithm Data Encryption Standard (DES) was developed by IBM in cooperation with the National Security Agency (NSA) in 1975. The objective of the developers was to create a standard for inter-agency encryption that was as secure as it was uniform. Today, DES is not considered sufficiently secure for many applications due to its short key length of only 56 bits. However, the key length can be increased with relative ease through multiple applications. Referred to as triple DES, or TDES, 3DES, or DESede, DES continues to be widely used for banking services.
Twofish
Twofish is a symmetric-key algorithm with key lengths of 128, 192, or 256 bits that has been in use since 1998 as the successor to Blowfish, which is also still in use. Twofish is not patented and has been released into the public domain. It is thus freely available to anyone for use.
RSA
RSA is an asymmetric method that can be used for both encryption and digital signatures. It was originally developed in 1977/78 by Ron Rivest, Adi Shamir, and Leonard Adleman at MIT. Its security is based on the mathematical problem of breaking down a large number into its individual prime factors. Since RSA is at least a factor of 1,000 times slower than encryption methods such as 3DES and AES, in practice this method is generally only used to exchange a key. Encryption of the actual data requiring protection, on the other hand, is performed symmetrically to ensure the greatest possible performance.
Advanced Encryption Standard (AES)
The Advanced Encryption Standard (AES) is considered the successor to DES and was published as a new standard by the National Institute of Standards and Technology (NIST) in 2000. The names of the three AES variants AES-128, AES-192, and AES-256 each refer to the selected key length. AES offers a very high level of security; it was not until more than ten years after its standardization that the first theoretical vulnerability was found, although this is of no relevance in practice. The algorithm is freely available and may be used without licensing fees as well as implemented in software and hardware. In the U.S., AES-192 and AES-256 are officially approved for government documents of the highest classification level.
08
Practical application scenarios
Encryption is an integral part of many digital solutions of our time. In particular, cryptography is used to protect communication on the internet from unauthorized access. Some application scenarios:
S/MIME
Secure/Multipurpose Internet Mail Extensions (S/MIME for short) is a standard method for encrypting and signing emails that is used primarily by companies. It enables companies to ensure both the integrity of the transmitted information and the identity of the sender. S/MIME uses hybrid encryption, in which the contents of the email are protected by symmetric encryption, while the key exchange is handled by an asymmetric method. S/MIME also relies on a hierarchical certificate system to authenticate public keys. To do this, companies and private users obtain the certificates they need for generating keys from central certificate authorities. Different classes of certificates are available depending on the level of authentication, and some certificate authorities also offer free certificates for private use.
PGP
Pretty Good Privacy (PGP for short), the tool developed by Phil Zimmermann, is also used to encrypt and sign emails. It follows a similar approach to S/MIME, but is primarily used for private purposes. Unlike S/MIME, with PGP trusted third parties “certify” the required keys—there are no central authorities in the “web of trust” made up of PGP users. For this reason, PGP and its free forks OpenPGP and GnuPG are also preferred by the open source community for securing emails.
KeePass
The open source password manager KeePass is used to manage login details locally on desktop systems. The open source solution uses symmetric encryption methods to secure the password database. Depending on the KeePass version used and user preferences, the AES, Twofish, or ChaCha20 algorithms are used. The encrypted database can only be accessed again by entering the previously defined master password. KeePass is primarily designed for use on Windows; other operating systems are covered by numerous forks of the project, such as KeePassXC, Keepass2Android, or MiniKeePass.
HTTPS
The HTTPS protocol (Hypertext Transfer Protocol Secure) allows the establishment of encrypted connections on the internet. Technically, HTTPS uses conventional connections via HTTP (Hypertext Transfer Protocol) in combination with encryption and authentication via SSL/TLS (Secure Sockets Layer/Transport Layer Security). SSL and its successor TLS secure data traffic as an additional cryptographic layer on the network. In practice, TLS is used almost exclusively today. Nevertheless, the encryption method is stilled referred to as “SSL/TLS” in everyday speech. TLS uses an asymmetric method for key exchange. The encrypted connection itself, on the other hand, uses a symmetrical procedure to avoid any loss of performance. SSL certificates, which site operators obtain from certification authorities, are required for the authentication of servers and domains.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.