New: Flexible service plans for Myra WAF. Learn more!
Home>
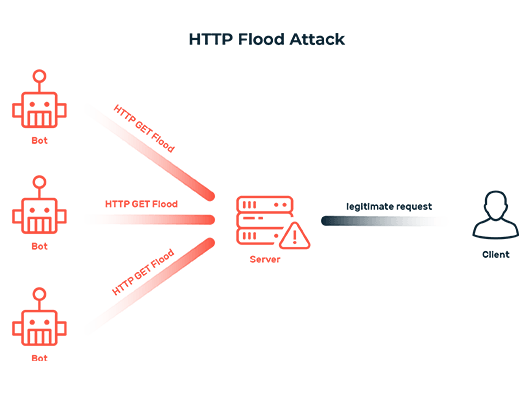
HTTP flood attack
03
What are the most frequent types of HTTP flood attacks?
The Hypertext Transfer Protocol (HTTP) provides several methods for exchanging data between a web browser and a website. By far the most commonly used are HTTP GET and HTTP POST. A GET request fetches information from the server without changing any data on it. With the POST method, data is sent to and processed on the server, such as content from a web form. HTTP flood attacks typically take advantage of these two HTTP methods:
HTTP GET flood
In an HTTP GET flood attack, the attacker (via a botnet) accesses a massive number of pages on a website that contain particularly large static content such as images. These files then have to be sent each time by the web server, which overloads it over time. As a result, it is no longer able to respond to legitimate requests, and the website or web application becomes inaccessible.
HTTP POST flood
In an HTTP POST flood attack, the attacker repeatedly sends data to the web server in order to increase the resources required on the server side to maximum capacity with each request. As a result, the server will sooner or later be incapable of providing any responses and the website or web application will no longer be accessible. Although this type of attack is more complex, it is also much more effective than relatively simple HTTP GET flood attacks. It causes even more damage with a similarly modest use of resources.
05
How can HTTP flood attacks be mitigated?
Once the attack traffic is identified, the requests associated with it can be rigorously blocked or discarded. This leaves the web server with sufficient resources to respond to all legitimate requests. An additional verification process can be used to ensure that legitimate requests are not inadvertently blocked or discarded: Requests classified as illegitimate can regain their status as legitimate requests by resolving a CAPTCHA. After being successfully verified, they are forwarded to the web server and responded to.
In any event, defending against HTTP flood attacks requires expertise and technology that only application layer (Layer 7) DDoS protection can provide. Protection systems for the network and transport layers (Layer 3 and 4), for example, are unable to distinguish between an HTTP GET flood attack and a valid download. Accordingly, reliably detecting attacks and safeguarding a website or web application requires DDoS protection on all relevant layers. This is the only way operators can prevent attack-related disruptions and downtimes, which are often accompanied by loss of revenue, image, and trust.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.