New: Flexible service plans for Myra WAF. Learn more!
Home>
Web application firewall (WAF)
At a glance
- 01. Web Application Firewall (WAF): A definition
- 02. How Does a Web Application Firewall (WAF) Work?
- 03. What Dangers Does a Web Application Firewall (WAF) Protect Against?
- 04. What Are the Advantages of Using WAF Security?
- 05. What Types of WAFs Are There?
- 06. Against What Can an Application Level Firewall Not Protect?
- 07. Which Companies Need a WAF?
- 08. What Do Companies Need to Consider When Using a WAF?
- 09. Web Application Firewall (WAF): What You Need to Know
03
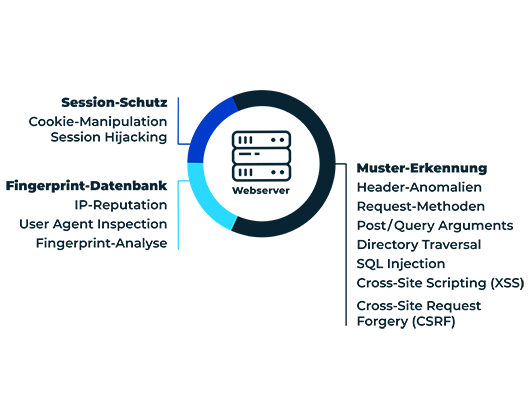
What Dangers Does a Web Application Firewall (WAF) Protect Against?
A web application firewall protects web applications against data theft, account takeover, malicious manipulation and sabotage. Among other things, organizations can protect themselves against the following attack patterns by using a WAF:
Cross-Site Request Forgery
With cross-site request forgery, attackers cause the user's browser to send manipulated HTTP requests to a website or web application in order to trigger unwanted actions.
Cross-Site Scripting (XSS)
In a cross-site scripting attack, cyber criminals inject malicious code into web applications by exploiting security vulnerabilities in order to steal sensitive information such as login data. Interactive websites and applications are particularly susceptible to this. As an upstream protective wall, a web application firewall prevents such malicious access.
SQL-Injection
With an SQL injection attack, cyber criminals specifically exploit security vulnerabilities to infiltrate manipulated commands or malicious code via input masks, for example. Dedicated rule sets allow WAF solutions to reliably detect and thwart injection attacks.
OWASP Top 10
The non-profit organization Open Web Application Security Project (OWASP) regularly compiles a list of the 10 biggest security problems for web applications. Many of the threats on this list can be addressed by a web application firewall.
Zero-Day Exploits
In the case of zero-day exploits, cyber criminals immediately use newly discovered software vulnerabilities such as Log4Shell or Confluence OGNL for their attacks. Adapted WAF rules offer immediate protection in such an acute threat situation until patches for the vulnerable software are available and applied.
04 - What Are the Advantages of Using WAF Security?
Companies that use a web application firewall on their website benefit from the following advantages:

Additional Security Layer for Web Applications
In combination with other security measures, an application level firewall provides an additional layer of protection against unauthorized access.

Closing Security Gaps in Multiple Applications
Webmasters can place a WAF in front of several applications at the same time. This procedure makes it possible to close existing security gaps.

Protection of Legacy Systems and Applications
Especially with software that has been in use for a significant period of time and has not been programmed internally, security vulnerabilities can persist for a long time. A WAF offers additional security here.
05
What Types of WAFs Are There?
There are three ways to set up a WAF architecture: Centralized as a network-based hardware appliance or virtual appliance, host-based directly on the web server, or a company uses a cloud SaaS solution. Depending on the type and deployment, the functionality and associated costs differ immensely.
Network-Based WAF
These web application firewalls are integrated into the network as hardware appliances or virtual appliances in front of or behind the web servers. The solutions offer high scalability and performance, but also require more bandwidth and a correspondingly high-performance infrastructure.
Host-Based WAF
Host-based web application firewalls are installed as software or modules directly on the same server on which the web application is hosted. They offer a high level of integration and control options, but also require more resources and high maintenance costs.
Cloud SaaS WAF
Numerous providers have developed software-as-a-service solutions for WAF use, which are hosted in the cloud and offer companies less internal effort while at the same time being highly flexible and cost-efficient. Especially with a managed WAF, configuration, maintenance and operation of a cloud web application firewall are carried out by the provider.
Discover our customized Security-as-a-Service solutions for IT infrastructures and web applications for yourself.
08
What Do Companies Need to Consider When Using a WAF?
A web application firewall is only as good as its filters and configuration. If you make a mistake here or are too restrictive, you can expect problems. Therefore, managing a WAF requires appropriate IT security specialists who have the resources available to take over the ongoing management of the firewall. Companies that cannot guarantee this internally rely on SaaS solutions from external providers to take over the administrative work.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
Deep Dive WAF IT-Security
In-house operation of a WAF (also known as an application level firewall or web app firewall) involves a great deal of effort. Depending on the type, considerable costs are incurred for the necessary hardware, software and operation – in particular, specialist personnel with in-depth knowledge of information security are often difficult to obtain. IT security service providers who offer WAF solutions as a service can help here.
Suitable service providers have the necessary industry experience to ensure efficient operation of the WAF services. The rule sets configured within the WAF must harmonize with the digital business processes of the respective organization. Otherwise there is a risk of downtime and performance losses. A customized configuration by the web application firewall provider is essential for this.
In addition, compliance requirements resulting from laws and regulatory provisions such as the General Data Protection Regulation (GDPR), the NIS 2 Directive or the IT Security Act must be observed when selecting a service provider. As a rule, highly certified providers based in the European Economic Area (EEA) are preferable from a compliance perspective.
An incorrectly or poorly configured WAF (sometimes also called a cloud WAF or WAF firewall) has a number of disadvantages. For example, a faulty implementation can impair the performance of web applications by causing additional latency or overhead. In addition, false positives or false negatives can jeopardize both the functionality and the security of web applications because legitimate user requests are blocked and malicious attacks are allowed through. All of this in turn causes additional costs for reconfiguration, maintenance and possible operational failures.
In addition, for the best possible protection performance, a web application firewall must be continuously monitored and optimized to keep pace with new threat patterns, fix potential bugs or vulnerabilities, and address new security policies.
When using a web application firewall, working with an experienced service partner is therefore usually the best option for ensuring the security (WAF Security) and performance of web applications.
A WAF (Web Application Firewall) is an important, but not sufficient, component for web application security that should complement, but not replace, other security and performance tools. Only in combination with other security and performance tools such as DDoS protection, bot management and load balancing can an application level firewall fully exploit its strengths and contribute to the holistic protection of critical business processes on the web.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.