New: Flexible service plans for Myra WAF. Learn more!
Home>
SSL/TLS termination: focus on compliance and trust
SSL/TLS termination: focus on compliance and trust
In order to detect hidden cyberattacks and accelerate website content, providers of security and CDN services must decode encrypted traffic. This technical requirement makes the choice of service provider a question of compliance and trust.

The absolute majority of all websites today are delivered over HTTPS. 97 of the 100 most popular websites globally rely on HTTPS by default, and all 100 support encrypted transmission. Content on these pages is encrypted using SSL/TLS certificates, guaranteeing their security and integrity to users. In particular, web applications on which sensitive data is processed, such as online banking, benefit from this additional layer of protection.
That's why HTTPS traffic must be decoded
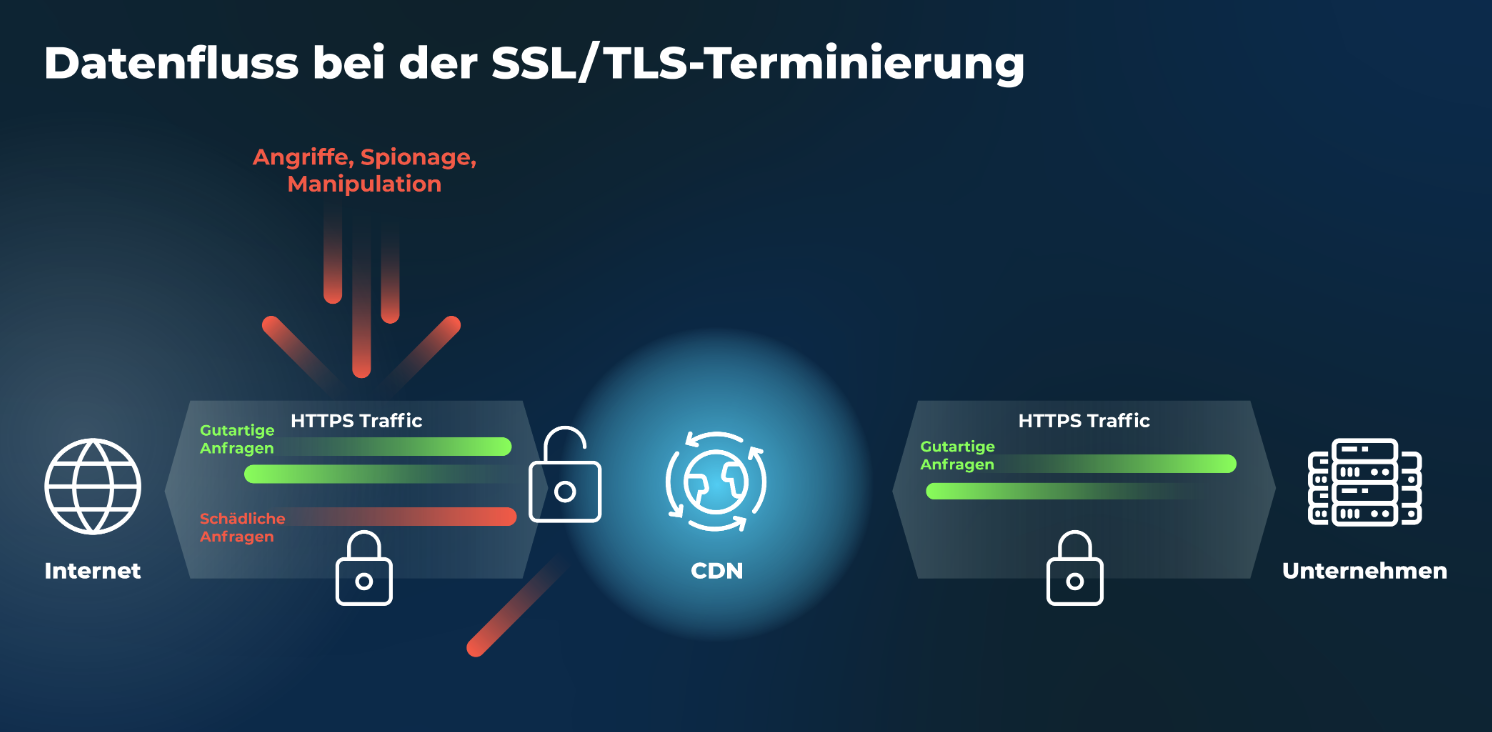
SSL/TLS encryption is used to ward off prying eyes and protect against sabotage and manipulation. However, the HTTPS protocol also makes it difficult to clearly identify malicious traffic and accelerate content for performance optimization. This is why content delivery services (CDNs) and cloud-based web application protection services require that encryption be decoded – this is known as SSL/TLS termination. Only when the traffic is decrypted does effective deep package inspection for granular filtering of the data stream become possible – this enables defense against encrypted attacks (port 443).
To enable decoding of the encryption, the private SSL/TLS keys must be sent to the service provider. However, decoding also gives this provider complete access to the transmitted data. Choosing a trustworthy and competent service provider for CDN services or web application protection is therefore crucial to ensure confidentiality, integrity, authenticity, and availability of the data.

Securing legal DSGVO compliance requires local data sovereignty
Since SSL/TLS termination also exposes personal data for short periods of time, this process is also extremely sensitive in terms of the applicable data protection regulations.
In general, the European General Data Protection Regulation (GDPR) allows the processing of such sensitive data exclusively in the European Economic Area (EEA) and in secure third countries for which an adequacy decision by the EU Commission exists. Data transfers to other countries, such as the USA, require the use of compensatory measures, such as solid encryption, to ensure the specified level of data protection.
However, implementing such encryption is not technically possible for CDNs and web application protection services. For this reason, the European Data Protection Committee (EDSA) currently sees no possibility of implementing compensatory measures that would permit legally secure use of the services, particularly regarding U.S. providers.
Compliance-compliant processing to the highest standards
Myra's services offer the highest level of security. Our customers' SSL/TLS certificates are stored in a secure area of our infrastructure. Downloading or viewing existing SSL/TLS certificates from the Myra platform is explicitly not possible. Decoding only takes place to verify the packets. All communication on our network to the outside world, to the user and to your Origin server, is fully encrypted. At Myra, SSL/TLS termination takes place exclusively in Germany on customer request – legally compliant with GDPR.
Security Insights
02 November 2020
Cyber warfare: US military succeeds in strike against the TrickBot botnet
Myra News
21 October 2021
ISO 27001 based on IT-Grundschutz (IT baseline protection): Myra Security renews strict BSI certification
Security Insights
17 May 2021