New: Flexible service plans for Myra WAF. Learn more!
Home>
IP stressers/booters
At one look
- 01. A definition of IP stresser/booter
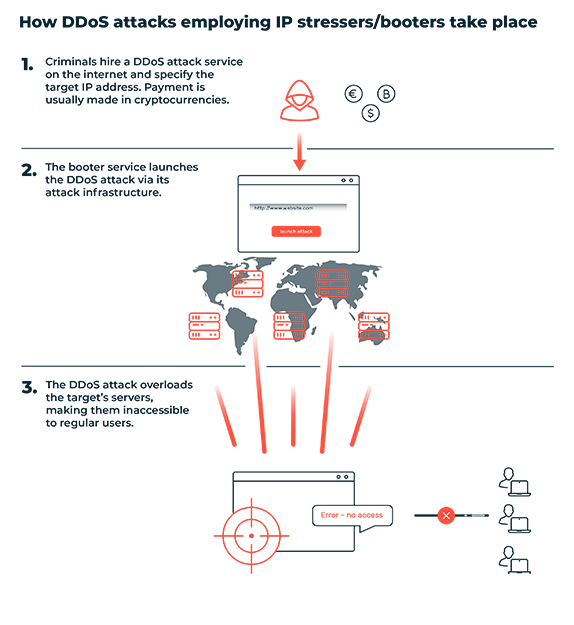
- 02. How does an IP stresser/booter work?
- 03. Are IP stressers/booters legal?
- 04. Known examples of IP stressers/booters
- 05. What risks are posed by IP stresser and booter services?
- 06. How can DDoS attacks be fended off?
- 07. What you need to know about IP stressers/booters
03
Are IP stressers/booters legal?
Most DDoS-for-hire service providers lend themselves a legal veneer by advertising their services as a stress test tool for website operators. This is also where the term “IP stresser” comes from. But by not requiring proof of identity when used and offering anonymous payment options, the providers open the floodgates to the illegal use of their services while also making law enforcement more difficult. As a general rule, stress tests performed on a company’s own IT infrastructure are perfectly legal. However, the unauthorized use of IP stresser or booter services against third-party targets is against the law in most countries. In Germany, this is considered computer sabotage under Section 303b of the German Criminal Code (StGB) and is subject to criminal prosecution. According to Europol, anyone who carries out a DDoS attack or develops, offers, or uses DDoS-for-hire services faces prison sentences and/or fines.
04
Known examples of IP stressers/booters
As previously mentioned, prosecuting users and operators of illegal IP stresser or booter services remains difficult. Nevertheless, investigators have repeatedly been successful in shutting down DDoS-for-hire services in the past few years:
vDoS
Until its closure in the fall of 2016, vDoS was considered the most reliable and powerful booter service in the cybercrime scene. According to research carried out by investigative journalist and IT security expert Brian Krebs, it was responsible for of more than two million DDoS attacks in total. According to the report, in the four months from April to July 2016 alone, vDoS generated 277 million seconds of DDoS traffic, equivalent to more than eight years overall. The service advertised attacks of up to 50 GBit/s – more than enough to take down websites or infrastructure without dedicated DDoS protection. In return, vDoS charged subscription fees of around $20 to $200 per month, which could be paid in Bitcoin or via PayPal. The two then 18-year-old operators of the illegal stress test provider were arrested in Israel in 2016 on behalf of the FBI. They also allegedly rented out their attack infrastructure to other booter services such as Lizard Stresser and PoodleStresser, earning more than $600,000 over a two-year period. In 2020, an Israeli court sentenced each of the two defendants to a minimum of six months of community service in light of their being minors at the time of the crime.
Webstresser.org
Webstresser.org was one of the world’s largest and most active DDoS-for-hire services before being taken offline by law enforcement in the internationally coordinated “Power Off” operation at the end of April 2018. For a subscription fee starting at $15 per month, criminals were able to launch multi-gigabit DDoS attacks via the service. According to Europol, shortly before its closure, Webstresser.org had more than 136,000 registered users and by then was responsible for around four million DDoS attacks. According to the German Federal Office for Information Security (BSI), they included overload attacks on several banks and numerous other financial and government service providers in the Netherlands in 2018, resulting in customers being unable to access their bank accounts for days on end.
Quantum Stresser
In a concerted effort by international law enforcement agencies, Quantum Stresser was shut down along with 14 other booter services in late 2018. According to the FBI, it had been active since 2012, making it one of the longest-running services of its kind. Quantum Stresser had more than 80,000 subscribers and was reportedly used to carry out roughly 50,000 DDoS attacks in 2018 alone. Investigators were able to track down the operator because he used the same email address for ordering home delivery of pizza that he had used to register his criminal attack service. In February 2020, due to his poor health, the then 24-year-old from the U.S. state of Pennsylvania was given a relatively lenient sentence of five years’ probation.
06
How can DDoS attacks be fended off?
DDoS attacks carried out by means of IP stresser or booter services pose a serious threat to companies in particular. To avoid financial damage and loss of reputation due to attack-related disruptions or outages, companies should take preventive measures to secure their web resources and IT infrastructure with dedicated DDoS protection for Layers 3, 4, and 7. Appropriate protection solutions can, for instance, be purchased as a managed service. They offer dynamic attack detection and filter out harmful traffic from the incoming data stream even before it reaches the company servers. As a service for companies and operators of larger websites, the BSI provides an overview of qualified DDoS mitigation service providers.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.