New: Flexible service plans for Myra WAF. Learn more!
Home>
DNS Spoofing
01
A definition of DNS spoofing
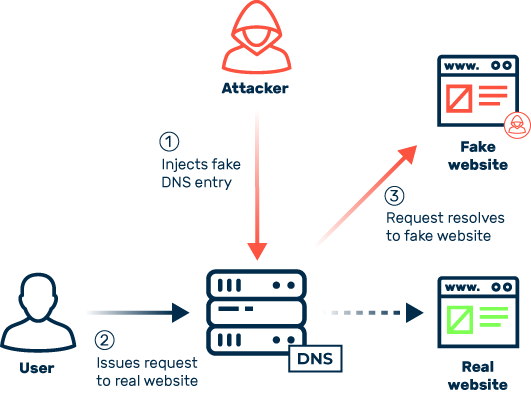
When cybercriminals misuse the DNS to maliciously redirect traffic with the intention of redirecting potential victims to fake and/or harmful content, this is called DNS spoofing. The word “spoof” means to parody, imitate, or fake. And that’s just what this attack vector does. In the vast majority of cases, cybercriminals use DNS spoofing for phishing attacks to get their hands on sensitive user credentials. Login information from banks or payment services, for example, is in particularly high demand.
To redirect traffic, attackers sabotage the DNS, which in a figurative sense acts as the telephone book of the internet and defines the assignment of domain names to the IP addresses of web servers.
The correct assignment is stored in the DNS entries, which are provided by name servers worldwide and temporarily cached locally on routers and computers. If attackers succeed in injecting false entries within this chain of information, whether locally on a user’s computer or directly on a name server, they are then able to control and redirect traffic at will. Since DNS queries are usually transferred unencrypted, attackers have many options for malicious meddling.
DNS spoofing belongs to the ranks of “man-in-the-middle” attacks (MITM for short), in which cybercriminals insert themselves unnoticed into the digital communication between users and services.
03
What kinds of DNS spoofing are there?
Technically, there are many ways to carry out DNS spoofing. In general, this attack vector includes all forms of attacks that compromise valid DNS entries, redirecting users to other content on the internet without them noticing. The most common methods of DNS spoofing are:
DNS cache poisoning
One kind of DNS spoofing is referred to as DNS cache poisoning. Attackers seek to manipulate the DNS entries in the cache of devices, routers, and servers. To do this, cybercriminals exploit vulnerabilities to tamper with the DNS entries of name servers, which are then loaded into the cache of requesting servers and devices and passed on.
DNS hijacking
DNS hijacking involves the use of malware that cybercriminals sneak onto routers and devices such as PCs and tablets. This malware modifies the network connection settings stored on the devices to redirect users to harmful websites without them even noticing. A popular example of such malware is the Windows Trojan Win32/DNSChanger. The executable EXE file is only a few kilobytes in size and tampers with the system’s DNS settings to secretly redirect traffic. The attackers’ objectives include phishing and click fraud. To do this, users are directed to pay-per-click ad banners, which in turn generates revenue for the cybercriminals.