New: Flexible service plans for Myra WAF. Learn more!
Home>
DNS
02 – What Types of DNS Servers Are There?
Various servers are used at different points for the Domain Name System. They are organised hierarchically and regulate the delegation of requests and responses.

DNS Root Server
The root servers of the DNS are responsible for the top level domains (TLD). As the highest authority in the hierarchy, they refer queries to the correct TLD name server. ICANN (Internet Corporation for Assigned Names and Numbers) coordinates the work of the root name servers. There are 13 such root servers around the world, which are made up of more than 1,600 server instances in anycast operation.

Authoritative DNS Server
Authoritative DNS servers access the domain name space of a specific zone in their database. Each zone has at least one authoritative name server that manages the zone data – the information emanating from it is considered valid.

Non-Authoritative DNS Server
Non-authoritative DNS servers pass on DNS information from external sources and are not responsible for a specific zone. Instead, they retrieve the required domain information from an authoritative DNS server when a request is made and store it in the cache.

DNS Caching Server
DNS caching servers temporarily store the information from other name servers for a certain period of time in order to answer incoming queries more quickly. The duration of this storage is determined by the authoritative name server.

DNS Forwarding Server
DNS forwarding servers are generally used in larger company networks and by internet service providers (ISPs). They receive DNS queries from clients and forward them specifically to other DNS servers in order to better distribute the network load and speed up the response.

Resolver
Resolvers are usually responsible for name resolution in a local network or on the client PC/router itself. Resolvers send requests to the DNS to resolve domain names to IP addresses.
04
Criticism of DNS
The concept of the DNS as the telephone directory of the web dates back to the early days of the internet, when there was no cybercrime, tracking or digital censorship. This is why encryption methods were not used for the transmission of DNS queries back then. By default, the transmission takes place unsecured in plain text. This vulnerability makes the technology a powerful tool for cybercrime, tracking or censorship.
DNS attacks
As DNS does not validate communication by default, the technology is extremely susceptible to malicious manipulation. Using DNS spoofing, cyber criminals can redirect data traffic to malicious websites in order to spread malware or steal user data.
Espionage
The DNS is largely unencrypted. There is therefore a risk that the connection between the client and DNS server can be spied on. DNS extensions such as DNSSEC provide a remedy here by being used to validate DNS queries.
Censorship
Both associations and commercial providers criticize the fact that domains can be censored via the DNS. There is also a risk that the technology could be misused for censorship via Geoblocking is misused. Authoritarian regimes use DNS blocks for political censorship, for example.
05 – DNS Extensions and Encryption Technologies
Over the years, several standards, extensions and encrypted protocols have been developed to eliminate functional weaknesses and security gaps in name resolution. Depending on the DNS provider or DNS service, different standards and extensions are supported for name resolution.

Dyn DNS
Dyn DNS stands for "dynamic domain name system". Such services enable the user to assign a fixed host name to dynamic IP addresses. One of the areas of application is the operation of a web server despite a dynamic IP address.

Extended DNS
Extended DNS (EDNS) enables the transport of DNS data in UDP packets. Such an extension of the DNS packet format proved to be necessary in the 1990s, as the restrictions in the previous DNS packets no longer met modern requirements.

DNSSEC
DNSSEC describes a series of security extensions for the DNS that guarantee the authenticity and integrity of the data transmitted via the system. By encrypting data transmissions in the DNS, the privacy and data security of users is ensured.

DNS over HTTPS
DNS over HTTPS (DoH) is currently one of the most common solutions for DNS encryption alongside DoT. With DoH, DNS queries and responses are sent in the secure HTTPS website protocol via port 443. This means that the transmissions can no longer be distinguished from conventional website traffic, which prevents targeted blocking. Compared to conventional DNS name resolution, DoH is less performant. DoH was standardized by the IETF in 2018 as RFC 8484.

DNS over TLS
DoT is a standard proposed by the Internet Engineering Task Force (IETF) (RFC 7858) for securing DNS connections. In contrast to conventional DNS queries, DoT establishes a secure TCP connection (Transmission Control Protocol) between the client and DNS server, which is authenticated and encrypted using TLS. Technically, name resolution using DoT takes place via TCP port 853.

DNSCrypt
DNSCrypt is a protocol that is used to encrypt, authenticate and optionally anonymize communication between the DNS client and DNS resolver. Data traffic to the DNS resolver is secured using asymmetric encryption. By default, DNSCrypt uses port 443. To anonymize DNS queries, DNSCrypt can be extended with Anonymized DNS technology, which is also compatible with the other encrypted protocols.

DNS over QUIC
DNS over QUIC (DoQ) is a new protocol that is being standardized by the IETF. DoQ aims to combine the advantages of encrypted name resolution with short latency times. For high-performance data transfer, DoQ uses the new QUIC protocol, which is also used in HTTP/3 and relies on TLS 1.3 for security.
06
What Are the Dangers of DNS?
Due to the existing vulnerabilities, cyber criminals can abuse the domain name system as a powerful weapon. For example, changes to the DNS delegation structure can be used to redirect traffic to malicious websites. It is also possible to spy on established connections or use DNS servers as a DDoS attack tool. The most common DNS attacks include:
Frequently Asked Questions About DNS
DNS stands for Domain Name System. This is a hierarchically structured global server network that regulates the assignment of domains to the corresponding IP addresses. The DNS thus serves as the "telephone book of the web", so to speak.
DNS services are used to answer name resolution queries. This allows web addresses to be assigned to the corresponding web servers. The technology relies on a hierarchically structured network of DNS servers that are distributed globally. Before DNS, name resolution was still carried out via local hosts files. This concept was not suitable for dynamic scaling on the Internet.
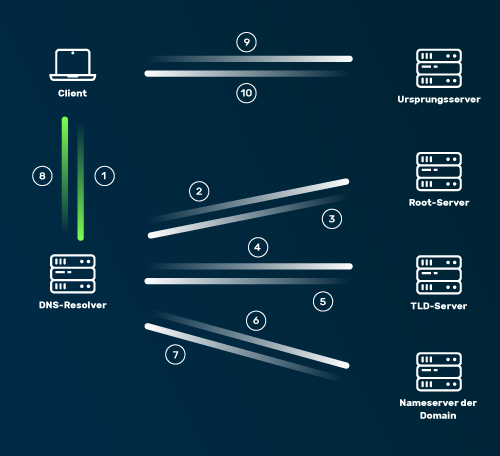
In detail, a DNS request follows the following pattern: 1. Enter the URL of a website in the browser (e.g. www.myrasecurity.com). The operating system checks the DNS cache based on the request. If the address is not in the cache, the request is forwarded to the DNS resolver. 2. The DNS resolver then contacts the DNS root server. 3. The root server tells the resolver under which top-level domain the information for the website can be found. In the case of www.myrasecurity.com, this is the top level domain (TLD) .com. 4. The resolver sends a request to the corresponding TLD server. 5. The TLD server specifies the IP address of the corresponding authoritative DNS server of the domain being searched for. 6. The DNS resolver asks the authoritative DNS server for the IP address of the origin server on which the website is hosted. 7. The name server forwards the address of the origin server to the DNS resolver. 8. The resolver forwards the IP address to the client's browser. 9. The browser now calls up the website by sending an HTTP request to the IP address. 10. The server addressed in this way sends the website files to the browser so that the content is displayed.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.