New: Flexible service plans for Myra WAF. Learn more!
Home>
Mirai
03
How does Mirai work?
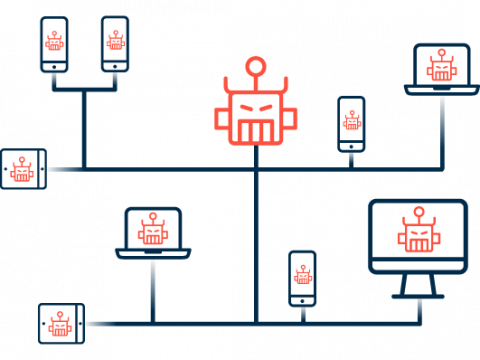
Mirai continuously scans the internet for publicly accessible IoT devices lacking password protection or using common factory default usernames and passwords. Once the malware has identified vulnerable devices, it tries a variety of default credentials to access the admin interface and report the infected devices to a “command and control” (C&C) server. The systems discovered using this method then become members (bots) of a botnet and can be remotely controlled via the C&C server to independently carry out a series of attacks and infect other devices. Insidiously, Mirai infections can occur without users actively downloading or executing the malware.
05
What risks are posed by botnets such as Mirai?
Malicious actors use botnets for a wide variety of attacks. Their motivation is usually financial. Botnet-based attacks can now even be purchased as a service for very little money, which means that criminals lacking the technical expertise can also exploit the huge potential harm caused by botnets for their own purposes. The range of criminal activities includes:
DDoS attacks
Using their own or leased botnets, cybercriminals often carry out DDoS attacks on websites, web applications, APIs, or IT infrastructure in order to overload the intended target with a massive volume of automated requests and thus bring it to its knees. The more bots are joined together, the more powerful the attack. Attackers often combine DDoS with blackmail: They threaten to carry out more overload attacks if the companies under attack do not pay protection money. The original Mirai authors also used their botnet for these criminal purposes.
Spam & phishing
Sending spam or phishing emails en masse is one of the most common uses of botnets. This is how criminals seek, among other things, to spread malware or to persuade unsuspecting users to divulge access data and other sensitive information.
Credential stuffing
By using a multitude of bots, attackers quickly test a huge number of user/password combinations via automated queries to webshops, online banks, or even company accounts. Confirmed credentials for active accounts are then sold on the darknet, or the information is used for more extensive attacks.
Proxy
Devices incorporated into a botnet can be used as proxies to hide their own IP address and thus surf the internet anonymously using third-party IPs. This is done by simply routing data traffic through the botnet.
Cryptominer
Some operators of botnets exploit the concentrated computing power of the devices they hijack to secretly mine cryptocurrencies and generate revenue directly.
Click fraud
Even the creators of Mirai used and rented out their botnet for click fraud. In this form of online fraud, bots are used to click on certain ads or affiliate links on websites in order to specifically manipulate the pay-per-click data of the advertising billing system, generating revenue at the advertiser’s expense.
06
Known attacks using Mirai
In 2016, the original Mirai botnet consisted of approx. 500,000 compromised IoT devices around the world. The botnet later grew to include several million devices. With this vast number of bots, cybercriminals carried out numerous attacks, especially in the early days of Mirai:
Minecraft server/OVH
The first known attacks using Mirai took aim at the servers of Minecraft, a popular online game. One of the victims was French hosting provider OVH, which was the target of one of the largest DDoS attacks to date in September 2016. In 2017 and 2018, additional attacks used Mirai to target Minecraft servers, such as the Minecraft Hypixel network.
KrebsOnSecurity
Also in September 2016, a DDoS attack carried out using Mirai resulted in the blog of investigative journalist and IT security expert Brian Krebs being unavailable for several days. Motivated by this, Krebs set out to uncover the identity of the creators of Mirai, which he succeeded in doing following months of research.
Dyn
In October 2016, a massive DDoS attack hit DNS service provider Dyn, forcing its servers to their knees. As a result, the American service provider’s customers were unavailable or only partially accessible for hours, including major players such as Twitter, Reddit, GitHub, CNN, The Guardian, Amazon, Netflix, and Spotify. The attack was carried out via the Mirai botnet, among others. The SpainSquad, Anonymous, and New World Hackers hacker collectives subsequently publicly admitted to being responsible.
Router/Deutsche Telekom
A worldwide attack by the Mirai botnet on selected remote maintenance interfaces of DSL routers crippled more than 900,000 of Deutsche Telekom’s network of Speedport routers in November 2016. Although the devices were not compromised, they still failed due to an internal error. As a consequence, affected Telekom customers were unable to make phone calls or go online.
Cybersecurity Solutions by Myra

DDoS Protection
Myra DDoS Protection provides you with fully automatic protection against malicious requests and overload attacks. Even in the event of an imminent attack, your web applications stay available at all times.

Hyperscale WAF
The Myra Hyperscale WAF protects your web applications against malicious access and vulnerability exploits. Thanks to simple integration and configuration, it can be set up in no time at all.

CDN
First-class user experience thanks to fast page loading and minimal latency: With the Myra High Performance CDN, all static and dynamic content on your website is delivered with high performance.
Secure DNS
Myra Secure DNS offers you a reliable and powerful solution for securing your critical web applications. Manage your name resolution with ease and protect yourself against DNS hijacking.
Deep Bot Management
Say goodbye to malicious bots forever. Myra Deep Bot Management creates unique fingerprints for each bot and thus enables an optimal response to every request.
Certificate Management
No more problems with expired SSL/TLS certificates. Increase the security of your digital assets with Myra Certificate Management and encrypt all your domains automatically.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.