New: Flexible service plans for Myra WAF. Learn more!
Home>
Darknet
03
What are the differences between the darknet, deep web, and clearnet?
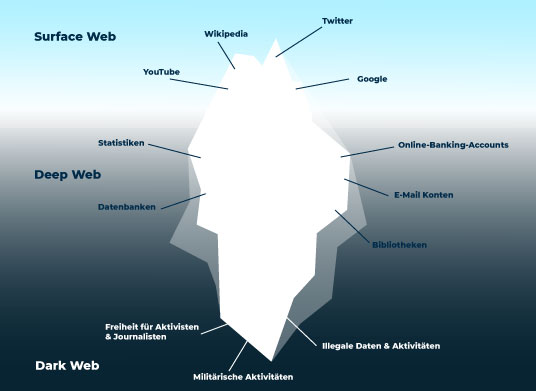
What exactly are the differences between the darknet, deep web, and clearnet? The iceberg metaphor is a great way to visualize it:
Clear Web:
This is the tip of the iceberg – the part of the internet we use every day. It is sometimes referred to as the surface web, visible web, or clear web.
Deep Web:
This is where, as it were, the user dives deeper and finds the part of the iceberg below the water’s surface. The content available here is only revealed if access protection can be bypassed via a password, etc.
Darknet:
A sub-area of the deep web that cannot be found by your ordinary “John Q. Public” – only those who have special tools can move about here, ensuring the necessary anonymity when surfing. It is impossible to access it without the right software, the appropriate browser setting, and, depending on the service, an invitation from another darknet user.
04
How do you get on the darknet?
Navigating the darknet requires the use of special client software. Different technologies are employed depending on the service:
Tor
Onion routing forms the technological basis of the Tor network. Its name comes from the structure of the encryption scheme used, which is secured several times over many layers. The connection is routed through a network of nodes that act as encrypting proxy servers. The most popular client for accessing the Tor network is the Tor Browser (an advanced variant of Mozilla Firefox) provided by the Tor developers themselves.
Hornet
Developed by researchers at ETH Zurich and the University College of London, “High-speed Onion Routing at the Network Layer” operates in a similar way to Tor – user data is reliably encrypted, making it impossible or extremely difficult to track.
I2P
Another alternative to Tor is the “Invisible Internet Project.” It differs from Tor in the sense that it does not use anonymous proxy servers; instead, everything on the network takes place decentrally and without servers. This enables full end-to-end encryption.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.