New: Flexible service plans for Myra WAF. Learn more!
Home>
Brute-Force-Attack
At one look
- 1. A definition of brute-force attack
- 2. How does a brute-force attack work
- 3. What kinds of brute-force attacks are there?
- 4. What tools are used in brute-force attacks?
- 5. What risks do brute-force attacks pose?
- 6. How can companies protect themselves from brute-force attacks?
- 7. What you need to know about brute-force attacks
03
What kinds of brute-force attacks are there?
Depending on the approach, there are a number of brute-force attack methods to choose from. The amount of information about the credentials being sought plays a key role.
Traditional brute-force attack
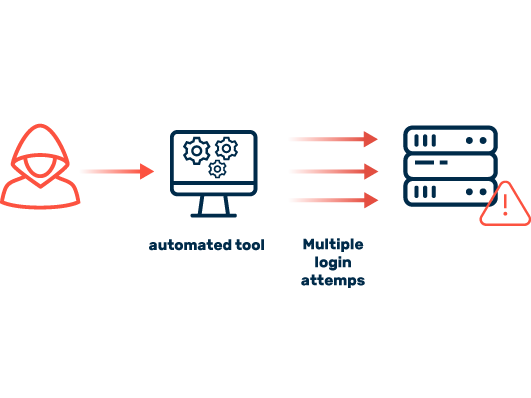
It is called conventional brute force if no information is available about the passwords or account names and the attackers are simply testing every possible combination of login credentials. The more powerful the hardware used, the faster passwords can be cracked. Special graphics cards are very well suited to solving cryptographic puzzles. This is why they are mainly used for mining digital currencies such as Bitcoin, since the hardware requirements are similar.
Credential stuffing
In credential stuffing, all of the credentials are already known, but not the service or platform they are used for. In this brute-force method, attackers take advantage of convenience on the part of users. Since, despite periodic warnings, many users still use the same email and password combination for multiple services, it is easy for cybercriminals to take control over a number of accounts once this information is known. Most stolen account info comes from hacks perpetrated on internet services. Whole lists of these records are being traded on the darknet. In order to act as quickly as possible and evade detection, attackers rely on botnets, which make countless concurrent login attempts in disguise, concealed behind a lot of different IP addresses.
Credential cracking
Unlike credential stuffing, in attacks employing credential cracking, all of the account credentials are not yet known. Attackers have the user name for a specific payment account, for example. But they don’t have the password. To get the password, attackers can either successively work through the passwords on lists of the most commonly used passwords or compute a completely random key. Botnets are again generally used to conceal and speed up the attacks.
Rainbow table attacks
Even if attackers have access to the passwords stored on the system, they are not normally stored in plain text, but only as hashes. “Rainbow tables” include the hash values of the most commonly used passwords. The passwords can be found by automatically comparing this data.
Dictionary attacks
As the name suggests, dictionary attacks employ existing lists of common user names and passwords to crack digital accounts.
04
What tools are used in brute-force attacks?
In addition to having the most powerful hardware possible, the software being used also plays an instrumental role in successful brute-force attacks. A number of common cracking tools have become popular among security specialists and cybercriminals alike:
Aircrack-ng
The Aircrack-ng name is behind a full suite of tools used to detect vulnerabilities in wireless networks. The software can be used on Windows, Linux, iOS, and Android. The program uses a dictionary of widely used passwords to crack Wi-Fi networks.
John the Ripper
John the Ripper (JtR for short) is an open source tool used to test authentication devices and is available for a variety of operating systems. The software uses a dictionary of the most commonly used passwords to test every possible login combination.
L0phtCrack
L0phtCrack is a password auditing and recovery application used to test password strength and sometimes to recover lost Microsoft Windows passwords by using dictionary, brute force, hybrid attacks, and rainbow tables.
Hashcat
Hushcat is primarily a password recovery tool that was originally proprietary but has since 2015 been developed as open source available for Linux, macOS, and Windows. The software recovers passwords based on their specific hashes.
DaveGrohl
This software is a free brute-force tool for Apple’s macOS. It was originally created as a hash extractor but has since evolved into a standalone password cracker.
Ncrack
Ncrack is a penetration testing tool used to crack network authentication quickly. It is designed to help companies maintain password security.
Brutus
Brutus is a free password cracker written originally to help check routers and other network devices for default and common passwords. The software supports HTTP (Basic Authentication), HTTP (HTML Form/CGI), POP3, FTP, SMB, and Telnet.
Hydra
Hydra is a login cracker which supports multiple concurrent connections and protocols. Penetration testers can use it to take a close look at multiple passwords on different systems simultaneously.
05
What risks do brute-force attacks pose?
In general, brute-force methods make it possible for attackers to compromise company accounts and systems. Depending on login options and hardware, even complex system encryption on mobile devices such as smartphones and notebooks can be cracked by brute force. Considerable harm may come from sensitive data records getting into the wrong hands. If the data wasn’t being properly secured, there might also be fines to face for lack of IT security and breaches of data protection law.
Credential stuffing and credential cracking have since become lucrative sources of income for cybercriminals on the internet. The online accounts hijacked by these methods are being sold at high prices on the darknet and are usually the starting point for more advanced cyberattacks. Attacks of this kind have serious consequences for companies. If attackers are able to take over the accounts of customers in spectacular fashion, any affected company can expect lower revenues and prolonged damage to their image.