New: Flexible service plans for Myra WAF. Learn more!
Home>
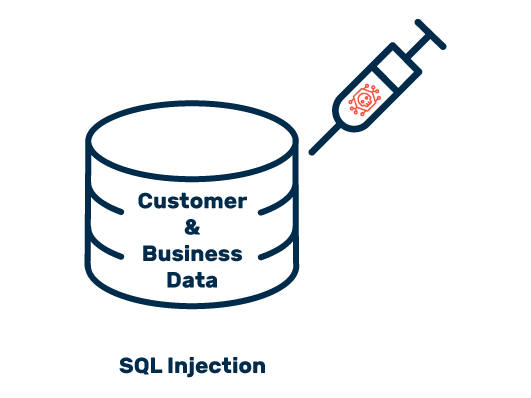
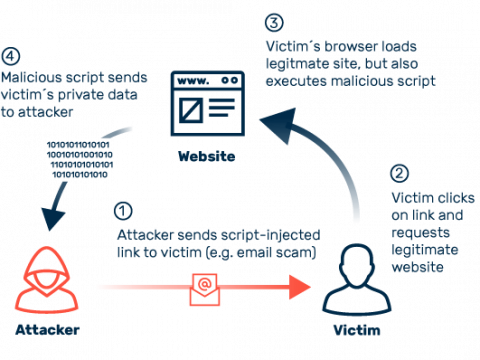
Code Injection
What you need to know about Code Injection
Injection attacks exploit vulnerabilities in the source code of websites. If these errors are not discovered when the page is created, in most cases the problematic code goes unnoticed until the consequences of an attack are felt.
Indications of injection attacks include uncontrolled data outflow, manipulation of user accounts or records, and error messages indicating corrupted files. In addition, atypical server queries are also indicative of injection attempts.
Since errors can never be ruled out, especially in the fast-moving digital industry with increasingly agile development, upstream protection solutions have become established as a proven means of defense against injection attacks. These technologies filter traffic based on predefined rules, differentiating between legitimate user requests and potential attacks.