New: Flexible service plans for Myra WAF. Learn more!
Home>
Spambot
03
How different kinds of spambots work
Form spam
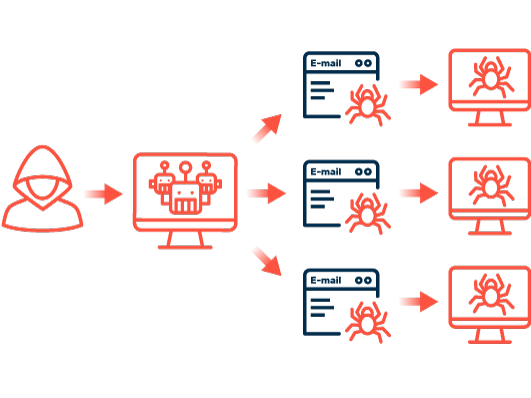
Bots are basically nothing more than scripts that independently perform predefined tasks. They can, for example, automatically comb the internet for websites that include forms, e-mail addresses, and other information. In the process, the spambot jumps from page to page by following the links embedded in them. In this respect, spambots are no different from their benign “colleagues.” Google Spider, to take just one example, is no different. It visits a web page, analyzes the content, sends information to Google’s servers, and then continues to the next page. An important differentiator between the two types of bots is their behavior when it comes to forms. Google bots do not fill out forms, but some spambots do.
Account creation & takeover
This allows malicious bots to create fake accounts on forums, social media platforms, in messaging apps, or with e-mail hosting providers. They can do this because creating an account often only requires filling out a few fields, such as the name or e-mail address. Attackers program their spambots to automatically fill out these forms. Some platforms employ CAPTCHAs or similar hurdles to prevent just this from happening, but these protections are not foolproof. Once the fake account is created by the spambot or another form of access to a platform is found, the bots start sending spam messages following a set of rules previously defined by the bot programmer.
To make this possible, other types of spambots engage in important preliminary work by collecting e-mail addresses or telephone numbers, which are then misused to send spam. This involves searching the internet, gathering contact information, and storing it in a database.
Spambots are programmed to work rapidly while consuming as few resources as possible. There are economic reasons for this: Operating a spam server incurs costs that must be recouped based on the principle of “mass, not class.” The goal is therefore to send as many spam messages as possible. Numerous bot instances run concurrently on each server and browse the internet simultaneously. To run more bots on each server, bots use simple requests sent to web servers. The returned HTML code is then analyzed. The accompanying CSS or JavaScript code is usually not interpreted to save resources and time.
04
Methods for identifying spambots
Spambots are only successful if they can perform their tasks while remaining undetected. During execution, for example, when entering spam messages into a comment form, they mimic the behavior of human users. Nevertheless, the activities of spambots can be detected using several methods:
Timestamps
The speed of spambots in particular can help distinguish access by malware from that of real people: Human visitors to a website typically take a certain amount of time to fill out a contact or comment form. In any case, if a human is involved, more than ten seconds should elapse between visiting a page and submitting the form. Bots, however, take only a few seconds for the same process. Timestamps can be used to measure how much time users spend on the website before completing and submitting the form. This time interval allows conclusions to be made as to whether the form was actually filled out by a human. The use of timestamps is an effective method of identifying spambots and preventing them from doing things like posting comments. Since human websites visitors do not have to become actively involved in this process, this is a user-friendly alternative to CAPTCHAs.
Honeypots
A honeypot is part of a website deliberately rendered invisible to human visitors. For example, a honeypot in the form of an additional input field is integrated into a form and then hidden using CSS or JavaScript. Humans always focus on the layout of the website and don’t fill out what they are unable to see. A spambot, on the other hand, focuses on the source code of the website. Since it is unable to recognize whether a specific input field is visible, it always fills in every field, including the honeypot. When the form is then submitted and processed, a short query whether or not the honeypot field has been filled in is all it takes to detect a bot.
Fingerprinting
Problematic, undesirable, and dangerous access by spambots can also be detected using “fingerprints.” When Myra Hyperscale WAF is used, for example, each time the website is accessed, more than 50 access attributes for the unique identification of the system used are included in the fingerprint. Myra has now stored over three million of these digital fingerprints. As soon as the fingerprint is obtained, appropriate measures can be taken and protective mechanisms initiated. Unwanted and prohibited access can be clearly identified, blocked, confronted with human interaction challenges such as CAPTCHAs, or otherwise controlled or redirected.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Björn Greif
Senior Editor
About the author
Björn started his career as an editor at the IT news portal ZDNet in 2006. 10 years and exactly 12,693 articles later, he joined the German start-up Cliqz to campaign for more privacy and data protection on the web. It was then only a small step from data protection to IT security: Björn has been writing about the latest trends and developments in the world of cybersecurity at Myra since 2020.