Discover how Myra combines digital sovereignty and cyber resilience.
Home>
Myra Security Presents Study on the State of Digital Sovereignty
Myra Security Presents Study on the State of Digital Sovereignty
MYRA NEWS | July 24, 2025
84.4% of IT decision-makers want European digital products for government and operators of critical infrastructure (KRITIS). Less than 25% of companies use European cloud services; AI infrastructure is only around 10%. Despite heavy dependencies, almost half of companies have no plans to switch to European software.

Myra presented a study on the state of digital sovereignty in Germany at the “BOTS & BREWS” media roundtable. (Photo: Matthias Balk)

Myra presented a study on the state of digital sovereignty in Germany at the “BOTS & BREWS” media roundtable. (Photo: Matthias Balk)
German companies are dependent on US software providers and are reluctant to switch. This is the conclusion of the report “State of Digital Sovereignty 2025” published by Myra. The company presented the results of a survey of 1,500 IT decision-makers at its media roundtable on cybersecurity, “BOTS & BREWS,” in Munich. The results reveal a clear discrepancy between the aspirations and reality of German companies in the area of digital sovereignty.
A clear majority (84.4%) call for the use of European solutions in the public sector and in critical infrastructure. However, US software continues to dominate their IT landscapes. This dependence is particularly pronounced in cloud services and cybersecurity: in both areas, around 40% of those surveyed consider themselves to be highly dependent on non-European providers.
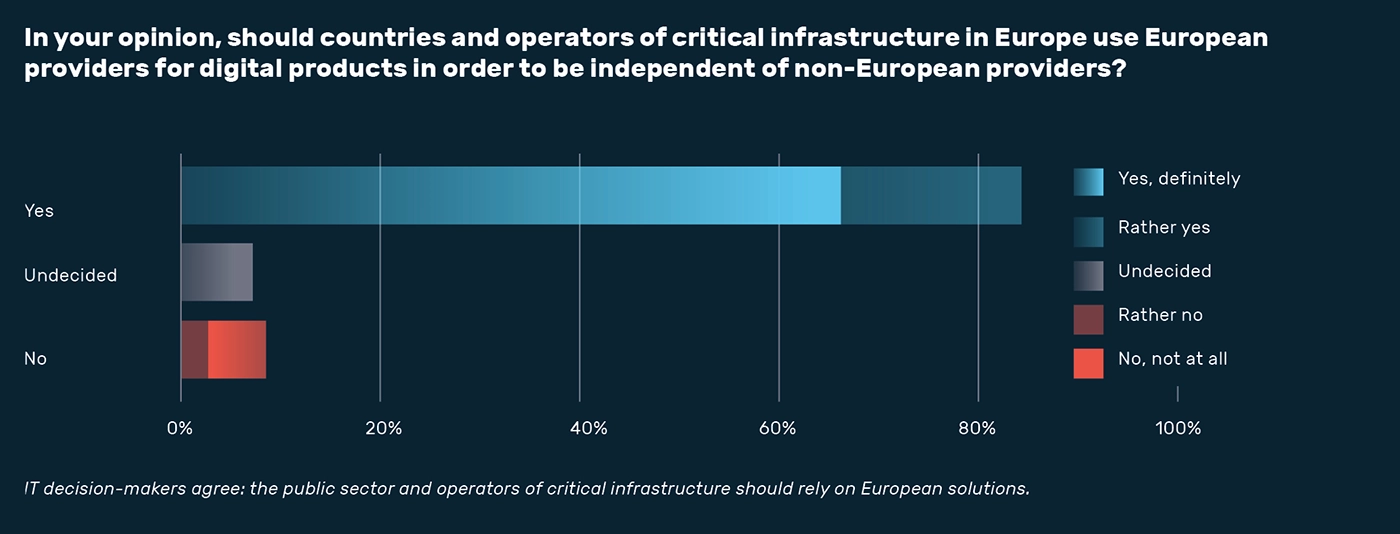

“Digital sovereignty means having decision-making options,” said Claudia Plattner, President of the German Federal Office for Information Security (BSI), at the presentation of the report. “In addition to international out-of-the-box solutions, competitive European products are needed, which already exist in certain areas. At the same time, we must secure international digitalization technologies in such a way that they are safer for us to use and, in particular, allow us to retain data sovereignty.”
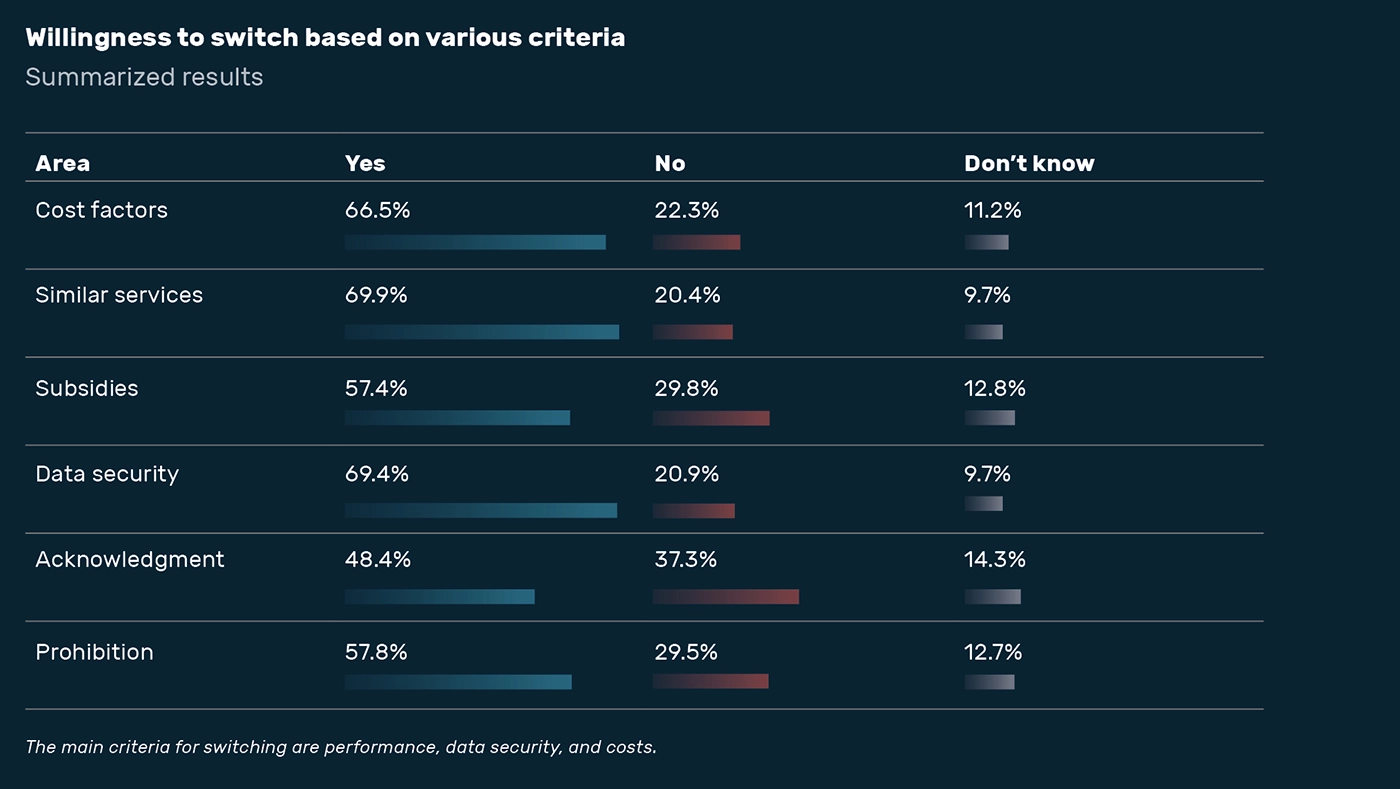
Only about one-third of companies plan to switch to European software within the next two years. Almost half (48%) rule out a switch. Clear requirements must be met in order to persuade decision-makers to make the switch:
Two-thirds would switch to European providers if performance and security were comparable.
For 62.5% of those surveyed, guaranteed data storage in the EU is a decisive criterion for the future use of European software.
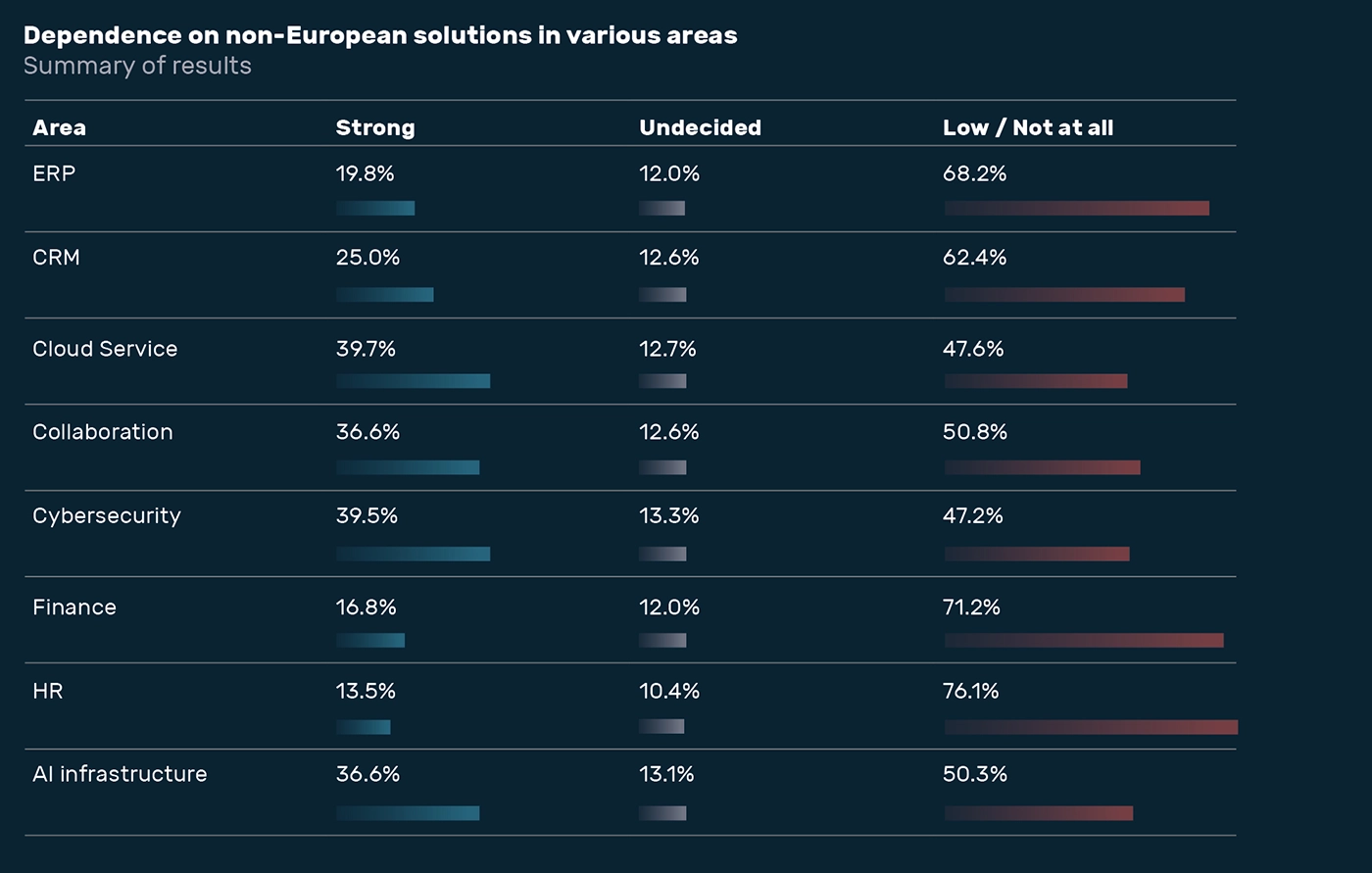

European alternatives are not only rarely used, but are often completely unknown. Nevertheless, many companies overestimate their own independence.
21.9% say they are familiar with European AI solutions.
Only 10.2% use them.
More than half (50.3%) nevertheless rate their dependence in this area as low or non-existent.
The picture is similar in cybersecurity. Only one in three is aware of European offerings. Only 20.5% use them. However, almost half (47.2%) see only a weak to non-existent dependence.

“Regional instead of global has become the credo of our decade,” says Dennis-Kenji Kipker, scientific director of the cyberintelligence.institute (CII). “This also means that we must now reclaim our digital sovereignty, which we have recklessly surrendered. Because a lack of digital sovereignty makes Europe's economy and IT vulnerable to blackmail – politically, economically, and technologically.”
About the author
Nicolas Armer
Global Communications Manager
About the author
As PR & Communications Manager, Nicolas Armer is responsible for public relations and the development of communication strategies. Prior to this, he worked as a PR consultant at the Munich-based agency Akima Media, where he primarily worked with international clients in the cyber security and data management industries.
Nicolas began his professional career as a soldier in the German army. He then completed a traineeship at the German Press Agency (dpa), which laid the foundation for his career in journalism. As a photojournalist, he worked for German and English-language media as well as for well-known companies for over eight years, reporting from various parts of the world. Today, Nicolas devotes himself to stories from cyberspace, undoubtedly one of the fastest-changing fields today.
