Myra Is Your Efficient Answer to DDoS Attacks
This Is Why CISOs Choose Myra
Our key benefits at a glance
Unlock the Power of Our Comprehensive Certification
Experience peace of mind knowing that our cutting-edge technologies, exceptional services, and streamlined processes are meticulously audited and certified to surpass the highest industry standards.
Embrace Quality with Our "Made in Germany" Assurance
As a company based in Germany, we strictly adhere to the stringent regulations imposed by the GDPR, ensuring that your data privacy is our top priority.
Experience Unmatched Support, Anytime, Anywhere!
Receive unparalleled assistance from a team of security experts, part of our reputable Myra Security Operations Center. We're available 24/7 to address any concerns and provide you with guidance.
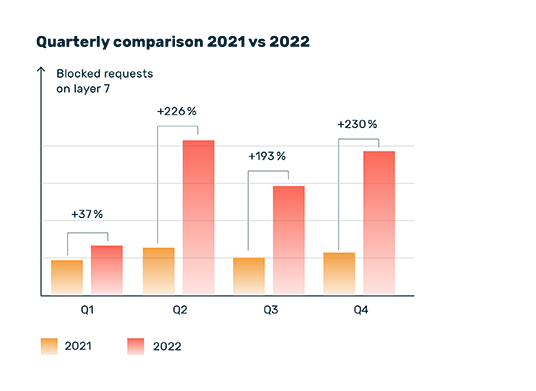
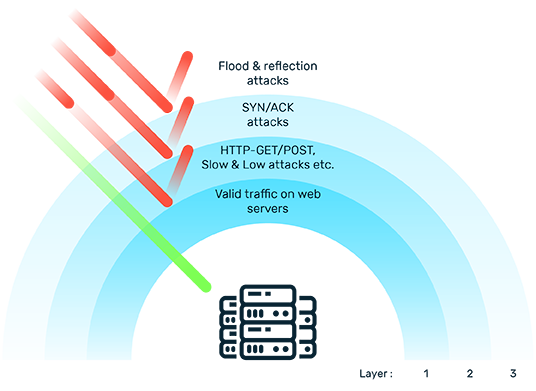
Myra DDoS Protection at a Glance
Key features
Advanced GeoIP Blocking
Myra DDoS Protection can block suspicious clients based on GeoIP information like region, country, or other IP characteristics.
Rate Limiting
Determine the number of web requests conspicuous IP addresses are allowed to make within a specified period.
Automatic Notification
In the event of an attack, have Myra automatically inform you based on your predefined escalation and notification levels.
Detailed Reporting
After the DDoS mitigation, receive individual reporting on the duration, type, and strength of the attack.
Upstream Monitoring
Myra monitors your upstream 24/7 and automatically notifies you of any communication issues with the origin server.
Certificate Management
Issue automated SSL/TLS certificates and keep track of everything with a centralized management system.
SSL/TLS Cipher Management
Enjoy the benefits of a continuously updated SSL/TLS configuration based on the latest security standards.
Broad Technology Support
Get seamless integration with Myra. We support modern web technologies such as HTTP/2, WebP, ChaCha20, WebSocket, and WebRTC.
Rely on IPsec
Get the encrypted forwarding of clean traffic for increased security requirements with this optional Myra feature.
Find out More About Our Other Protection Solutions for Web Applications.

Hyperscale WAF
Attackers exploit vulnerabilities in web applications to penetrate vulnerable systems and manipulate, steal or delete data. Myra's Web Application Firewall (WAF) blocks malicious requests before they reach your servers.
Deep Bot Management
Combat bot-driven threats that degrade your website's performance and compromise your data. Myra's advanced Deep Bot Management identifies and mitigates malicious bots, protecting your resources and ensuring a smooth user experience.
Secure DNS
Name resolution protection is critical to the resilience of critical web applications. The hardened and geo-redundant Myra Secure DNS uses leading technologies to protect your domains from cyberattacks and ensure maximum performance. Entire DNS zones can be conveniently managed in the secure Myra infrastructure.
Certificate Management
Build trust with users of your services and secure data transmission with Myra Certificate Management. Issue and easily manage SSL/TLS certificates to enable unique authentication and data integrity. Automate the process and ensure seamless protection for your website.
Analytics Data Lake
Get strategic intelligence to optimize your web resources with Myra Analytics Data Lake's comprehensive monitoring and reporting capabilities. Gain valuable insights by retrieving, searching, and analyzing log data in real time. Stay informed and make data-driven decisions to improve performance.

High Performance CDN
High speed, low latency and flexible scalability: The demands on modern web applications are growing visibly. With the Myra High Performance CDN, you can achieve a first-class user experience thanks to leading technologies.
Push CDN
Move static elements of your website directly to the Myra Push CDN and benefit from geo-redundant high availability, optimal performance and advanced resilience.
Video Streaming
Meet the needs of today's users with Myra's adaptive video streaming capabilities. Seamlessly adapt your streams to changing bandwidths, connection speeds, and network types. Deliver a superior streaming experience - anytime, anywhere!
Multi Cloud Load Balancer
Improve user experience with low latency and optimized load balancing with Myra's Multi-Cloud Load Balancer. Effectively distribute incoming requests, balance the load across multiple backend servers, and achieve faster response times. Keep your web applications running smoothly and efficiently.
Don't Let Cyber Threats Take Over: Request Your Personal Demo Now!
Don't wait for a cyberattack to protect yourself. Discover in just 30 minutes how Myra can help you and your team defend against cyber threats to keep your business secure.
What you can expect:
✔ Experience our Security as a Service Platform: Explore our cybersecurity platform from both an administrator's and an end-user's perspective.
✔ Real-time Consultation: Get immediate solutions from our cybersecurity specialists. They will help you understand how our solutions align with your specific requirements.
✔ Compliance Competence: Find out how you can ensure first-class availability, integrity and confidentiality of your data with Myra.
Now is the time to take the first step towards a better protection of your digital business.
Frequently asked questions about DDoS protection
DDoS protection refers to systems for defending against or mitigating cyberattacks by means of distributed denial of service. DDoS aims to cause delays and failures of websites and IT infrastructures via artificial requests. DDoS protection solutions are available either as a hardware appliance to be deployed in your own data center or as a security-as-a-service solution via the cloud. Cloud-based DDoS Protection can be deployed without additional hardware or software and therefore requires less effort to implement. Configuration and operation of the DDoS Protection is handled by the service provider. DDoS protection as a hardware appliance, on the other hand, requires a high level of expertise to implement and configure the protection solution efficiently in the company's own data center. A middle ground is described by on-premises services, where the DDoS protection is installed and operated by the protection service provider itself in the customer's data center.
The cost of DDoS protection varies depending on the desired deployment model (cloud, hardware or on-premises) and the required traffic bandwidth and number of domains to be protected. As a rule, security-as-a-service models for defending against DDoS attacks are more favorable for most companies than the in-house solution in their own data center. Here, full-service operators take over the initial implementation, continuous operation and configuration adjustments of security systems. Continuous monitoring of the secured systems is also included in order to ward off attacks as quickly as possible. Recruiting cybersecurity experts in particular is a major obstacle and often significantly slows down the commissioning of hardware appliances. According to Bitkom, 137,000 positions for IT experts across all industries are unfilled in Germany (as of Nov. 2022). On average, it takes seven months to find suitable candidates for open positions.
DDoS protection identifies harmful traffic flows and diverts them to free up capacity on the web servers for regular user traffic. Modern protection systems automatically initiate mitigation within a few seconds as soon as the previously defined threshold values (bandwidth, packet rate) are exceeded. In the event of an attack, high-performance scrubbing centers discard the requests, most of which are generated by botnets. Traffic flows are typically redirected in DDoS prevention using DNS or BGP.