New: Flexible service plans for Myra WAF. Learn more!
Home>
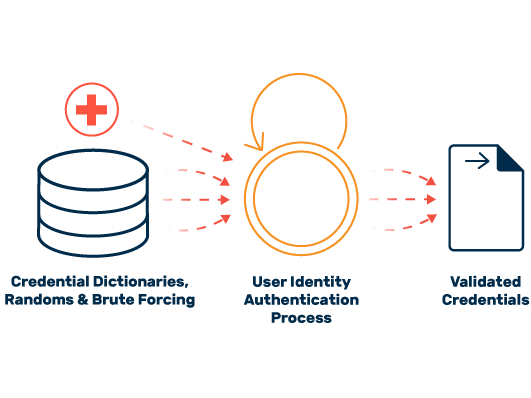
Credential Cracking
What are the consequences of credential cracking?
Depending on the extent of the attack, the affected companies can expect far-reaching consequences and high losses. Credential cracking usually targets extremely valuable accounts with wide-ranging access rights, which form a good basis for more extensive cyberattacks, manipulation, and industrial espionage.

Image loss
Affected customers and partners lose confidence in your company and look for alternative products and services from competitors. When in doubt, it takes years to rebuild trust once lost.

Image loss
Affected customers and partners lose confidence in your company and look for alternative products and services from competitors. When in doubt, it takes years to rebuild trust once lost.

Manipulation and espionage
If the stolen accounts are corporate accounts for CRM systems, for example, attackers can manipulate or steal sensitive company data. This misuse can cause lasting harm to companies and businesses.
How can companies protect themselves from credential cracking?
Defending against credential cracking involves the same measures as for credential stuffing. It is thus essential for companies to master a balancing act of security and usability for both cases. For one, wherever possible, complex and strict password security requirements must be introduced. For another, customers and business partners must not be put off by them.
In addition to password specifications and restrictions for common character strings and default passwords, an additional layer of security in the form of two-factor authentication (2FA) is also advisable.
Even if attackers should succeed in cracking the credentials, the account will still be protected by a 2FA code prompt, which can only be unlocked via a code application on the user’s phone or optionally via a code sent by text message code or the like. But even 2FA does not provide complete security. In the past, text message codes for 2FA have often been intercepted.
However, systematic control of bot requests has proven to be an effective means of protection against the misuse of credentials. Any suspicious attempts to access individual accounts can be reliably detected and blocked using bot management.
Myra protects your web services from credential cracking
With Myra Application Security and its integrated Deep Bot Management, Myra Security offers an upstream protection instance that protects web applications from credential cracking. High-performance Myra technology monitors, analyzes, and filters malicious internet traffic before virtual attacks cause any real damage.
About Myra Application Security