New: Flexible service plans for Myra WAF. Learn more!
Home>
Healthcare





Fortify Your Digital Defenses With Myra
4 key areas – 1 outstanding technology
Security
Avoid data theft, system outages, and disrupted communications. Our robust defense system protects your critical processes with unwavering vigilance.
Performance
Experience high-performance delivery of your content, even during traffic peaks. Maintain optimal performance and provide your users with a seamless experience.

Business Continuity
Myra ensures the utmost protection for your business by utilizing direct and geo-redundant connections to your infrastructure, without relying on external factors.
Compliance
Meet the requirements of IT security and data protection teams with ease. Myra is your trusted partner, offering unrivaled expertise in the strictest compliance regimes.
Designed and engineered for highly regulated sectors
Certified Security from Myra: Compliance Without Compromise
ISO 27001 on the basis of IT-Grundschutz (BSI)
Payment Card Industry Data Security Standard (PCI DSS)
BSI C5 Type 2
KRITIS Proof according to § 8a para. 3 BSIG
Trusted Cloud Service
IDW PS 951 Type 2 (ISAE 3402)
VS-NfD







Do you have
questions?
Please contact us via contact form or call us at:
+49 89 414141 - 345.
Protect sensitive patient data from harmful traffic
FAQ: Healthcare and Cybersecurity
It is obvious why cyber security solutions are a must in healthcare. Healthcare organizations need to develop and implement a comprehensive security strategy to protect themselves against cybercrime. This strategy should include both technical and organizational measures. Equally important are regular audits, reviews, and updates of security measures. Training and awareness programs for practitioners and patients also play a crucial role. They increase awareness of cyber threats and help to minimize the risk of attacks.
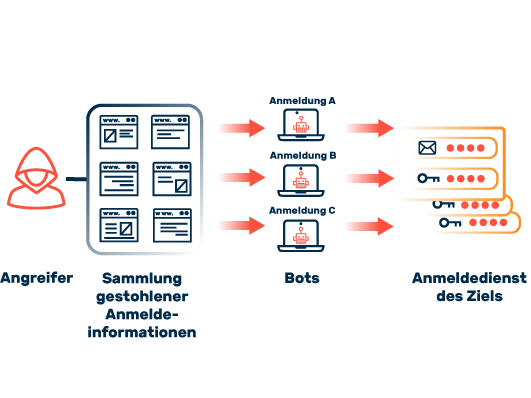
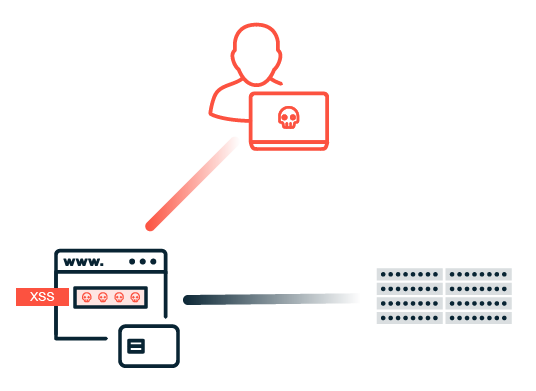
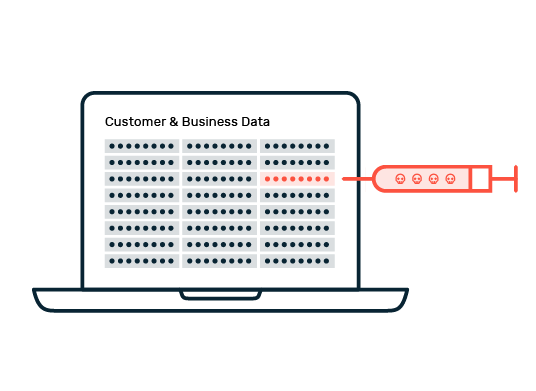
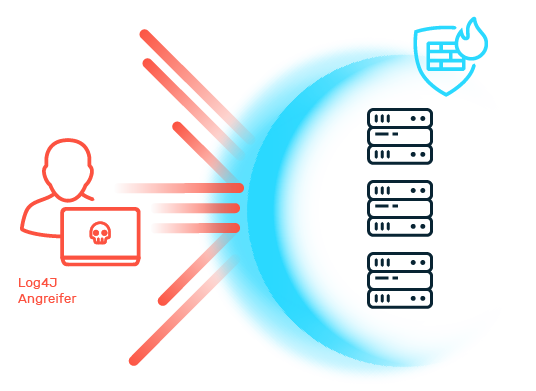
The healthcare sector is highly vulnerable to various forms of cybercrime. The most common threats include attacks such as denial of service (DoS) and distributed denial of service (DDoS), which aim to disrupt the availability of services. Ransomware and phishing attacks also pose a serious threat to hospitals and other medical facilities. Attackers attempt to extort high ransoms or steal sensitive patient data that is traded at high prices on the darknet. Social engineering exploits human weaknesses to gain access to confidential information or initiate fraudulent activities. It is often only when an actual attack occurs that it becomes clear whether the IT security measures of healthcare organizations are sufficient to defend against such threats.
The NIS-2 Directive and the Patient Data Protection Act (PDSG) are two important regulations aimed at improving cybersecurity in the healthcare sector and other critical sectors. The NIS 2 Directive harmonizes the cybersecurity requirements for critical infrastructures and essential services in the EU. It places particular emphasis on effective risk management and the obligation to report security incidents. The PDSG focuses on the protection of patient data and ensuring the confidentiality, integrity, and availability of this data in medical facilities. It requires healthcare organizations to implement robust security measures to protect sensitive information from cyber-attacks. Both regulations emphasize the need to develop and implement proactive security strategies to strengthen resilience to cyber threats.