New: Flexible service plans for Myra WAF. Learn more!
Home>
What is "DDoS"?
At one look
- 1. What is „DDoS“?
- 2. What Does a DDoS Attack Look Like?
- 3. Distributed Reflection Denial of Service Attack (DRDoS)
- 4. Who Are the Attackers?
- 5. Targets of DDoS Attacks
- 6. What Methods Do Attackers Use?
- 7. AI Botnets and AI Operators Increase DDoS Risk
- 8. Case Study: DDoS Attack Wave Before Austrian National Elections
- 9. When is DoS/DDoS a criminal offense?
- 10. What Are the Consequences of an Attack?
- 11. Why the IoT is a DDoS accelerator
- 12. Which Industries Are Affected?
- 13. How to prevent DDoS attacks
- 14. Evolution of DDoS attacks
- 15. Insights from the Myra Security Operations Center
4. Who Are the Attackers?
The motives of the attackers are varied. They range from blackmail and destruction to political protest or boredom. However, the goal is always the same: to slow down and paralyze the targeted applications and infrastructures with artificial requests.

Script Kiddies
The term “script kiddies” is primarily used to describe cyber attackers with limited technical skills who use ready-made tools and freely available scripts for their attacks. Although they are often dismissed as “amateurs”, their actions can cause considerable damage - especially if the attacked applications and infrastructures do not have dedicated protection systems.

Cybercriminals & Hacktivists
The absolute majority of all DDoS attacks are carried out by cybercriminals and hacktivists. While cybercriminals primarily pursue monetary goals with their attacks, for example to extort ransom money, hacktivists strive to cause as much damage as possible with a high public profile in order to pursue a political agenda with the resulting uncertainty among the population.

State-Sponsored Cyber Actors
In hybrid warfare, state cyber actors of authoritarian regimes use DDoS attacks to destabilize the infrastructure of enemy countries. Examples of this include attacks on energy suppliers or government networks, which are increasing in the wake of geopolitical tensions. Such attacks are often part of larger cyber warfare strategies.
05
Targets of DDoS Attacks
DDoS attacks are not just a technical challenge; they are often part of a larger strategy by cybercriminals. The target of these attacks can be multi-faceted and it is crucial to understand the motives behind the attacks to take effective security measures.
Blackmail and financial motivation
A widespread aim of DDoS attacks is to blackmail companies. Attackers often use DDoS attacks as leverage to demand a ransom. They threaten to disrupt a company's services for a certain period of time unless they receive payment. This can be particularly devastating for companies that rely on their online presence.
Damage to reputation and crowding out competition
DDoS attacks can also be used to damage a company's reputation. If a company is offline during an attack, this can deter potential customers and damage credibility. In highly competitive industries, some players use DDoS attacks to weaken competitors or reduce their market share.
Spreading political or activist messages
Sometimes DDoS attacks are a tool of activism. Groups campaigning for social or political change use DDoS attacks to draw attention to their causes. These so-called “hacktivists” see their actions as forms of protest, even if in many cases they enter legal and ethical gray areas.
Distraction for other attacks
DDoS attacks can also be used as a distraction to carry out other, more subtle attacks. While an organization's IT department is busy fending off the DDoS attack, attackers may attempt to infiltrate the network and steal sensitive data. This tactic underscores the need for a holistic approach to security that does not view DDoS protection in isolation.
Exploring vulnerabilities
Another reason for DDoS attacks can be the intention to test a company's defense mechanisms. Cybercriminals can use DDoS attacks as a way to find out how well a company responds to such threats and what vulnerabilities may exist.
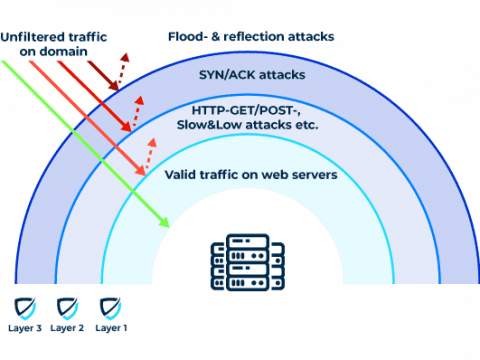
DDoS Attacks on Layers 3 and 4
CP SYN floods and UDP-based reflection attacks are among the most frequent attacks on the network and transport layer (layers 3 and 4). Other typical methods of attack include ICMP flood, UDP fragmentation, UDP amplification via DNS, NTP, rpcbind, SSDP, ACK flood, and RST flood. All of these attacks either overload the target with very high bandwidth or enormous packet rates. Legitimate attempts to access the data channel to establish communication are no longer possible.
In a SYN-ACK flood attack (or SYN and ACK floods), for example, a botnet remotely controlled by attackers bombards a server with SYN packets. They are usually part of what is called at three-way handshake, which occurs when a TCP connection is established between client and server. A SYN/ACK attack produces a huge number of half-open connections by sending many SYN, but none of the ACK packets needed to establish a full connection. As a result, no new connections can be established and the website is no longer accessible.
Myra Cloud Scrubbing protects IT infrastructure against such volumetric attacks on the network and transport layers. Detailed traffic analyses are provided by automatic flow monitoring. The failover of affected networks in case of an attack is fully automated.
DDoS Attacks on Layer 7
DDoS attacks on the application layer (layer 7) are based on connections that have already been established and have become one of the most common forms of attack. HTTP GET, POST, and other flood attacks as well as low and slow attacks are particularly popular with cybercriminals. They seek to penetrate the weakest component of an infrastructure, causing an overload of the web application.
For example, an attacker uses an HTTP GET flood attack to flood a web server with HTTP requests that specifically request pages with a large load volume. This causes the server to overload and it is no longer able to process legitimate requests. As a result, the website is no longer accessible to users.
Attacks on the application layer are usually not detected by the sensors used to protect the network and transport layers. Since they consist of standard URL requests, flood attacks are difficult to distinguish from normal traffic. Layer 3 and 4 protection systems, for example, cannot distinguish between an HTTP GET flood attack and a valid download. Accordingly, securing a web application requires IT security on all relevant layers. Specifically, attacks aimed at stealing sensitive data can only be detected and fended off by using Layer 7 protection.
Myra DDoS Web Protection protects web applications on layer 7 fully automatically. With full traffic visibility, Myra enables intelligent load balancing and site failover with high reliability and minimal response times.
07
AI Botnets and AI Operators Increase DDoS Risk
The widespread availability of large language models (LLM) and other AI solutions is exacerbating the cyber threat situation. Attackers are abusing these advanced technologies to disguise DDoS attacks, adapt their attack methods to existing defenses and search for vulnerabilities in applications and infrastructures.
The integration of AI technologies into DDoS attacks leads to a qualitative and quantitative escalation of the threat situation. AI-driven botnets such as Zergeca or DDoSia use advanced technologies such as DNS-over-HTTPS (DoH) for obfuscated communication and automated attack adaptations in real time. These systems analyze vulnerabilities much faster than traditional tools - newly published vulnerabilities are exploited within hours to generate tailored exploits that combine targeted WAF evasion techniques and multi-vector attacks.
AI operators also enable dynamic attack patterns: algorithms continuously vary parameters such as packet sizes, header data or query frequencies during ongoing attacks in order to outwit mitigation systems. The ability of modern AI bots to imitate human usage patterns (e.g. click behavior, session duration) is particularly critical, which makes it considerably more difficult to differentiate between legitimate access and attack traffic.
What Are the Consequences of an Attack?
An attack always harms affected companies and institutions, regardless of which method is chosen. Victim organizations still suffer from the consequences even years later. It is therefore extremely important to be adequately protected against DDoS attacks.

Economic Damages
A few minutes offline can quickly cost thousands of euros. Lost profits and wasted marketing budgets are only one example of the financial damages suffered.

Image Damage
The extent of damage to a company’s reputation caused by a successful DDoS attack is incalculable. Recovery costs a great deal of resources and may take years.

Data Theft
During a DDoS attack, systems no longer operate normally. The heavy load or overload causes some systems to suddenly become vulnerable and opens up new vectors of attack.
14
Evolution of DDoS attacks
The frequency and intensity of DDoS attacks has continued to increase exponentially in recent years. While the strength of attacks increased massively in 2013 due to the use of DNS servers for DRDoS attacks, the attacks reached a new dimension in 2016 with the Mirai malware. This malware used a botnet of over 100,000 IoT devices to carry out a 1.2 Tbit/s attack on the service provider Dyn. In 2018, the coding platform GitHub was overloaded with traffic spikes of 1.35 Tbit/s and another US company experienced an attack with over 1.7 Tbit/s.
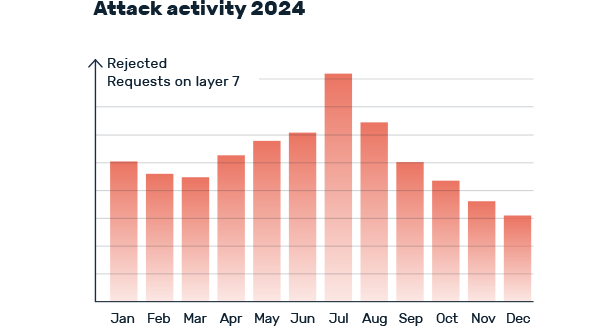
The situation has worsened in recent years. In 2024, the number of attacks fended off by Myra increased by 25 percent compared to the previous year. The public sector, the financial and insurance industry and critical infrastructures are particularly affected. The intensity of attacks has also increased: A record value of 5.6 Tbit/s was reached in October 2024. Complex attacks with multiple attack vectors have also increased.
FAQ on DDoS attacks
DDoS stands for Distributed Denial of Service and describes cyber attacks that cause delays and outages of websites via artificial requests. In contrast to conventional DoS attacks, with DDoS the malicious traffic streams originate from different sources (usually a widely branched botnet), which makes it more difficult to defend against.
In general, DoS/DDoS attacks on a service on the Internet are considered computer sabotage in Germany in accordance with Section 303b of the German Criminal Code (StGB) and are therefore also subject to criminal prosecution. It does not matter whether the attack has a criminal background (e.g. for ransom demands) or is carried out as part of a politically motivated protest action.
In a DDoS attack, cyber criminals cause a large number of artificial requests to a targeted service on the internet. As soon as the victim's web servers are overloaded by the incoming requests, there are delays and outages of the affected service. If no countermeasures are initiated (activation of DDoS protection), the problems continue until the attacker stops the attack.
DDoS attacks cause malicious load on websites and data centers. The attackers aim to cause delays or complete failures. Cyber criminals usually use botnets for the attacks, which bombard the intended target with huge numbers of requests.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.