New: Flexible service plans for Myra WAF. Learn more!
You're in Good Company When You Choose Myra









![]init[](https://www.myrasecurity.com/assets/79302/1674209677-init_logo_farbe_190x74-1.png?auto=format)














Your Daily Challenges Are Our Mission

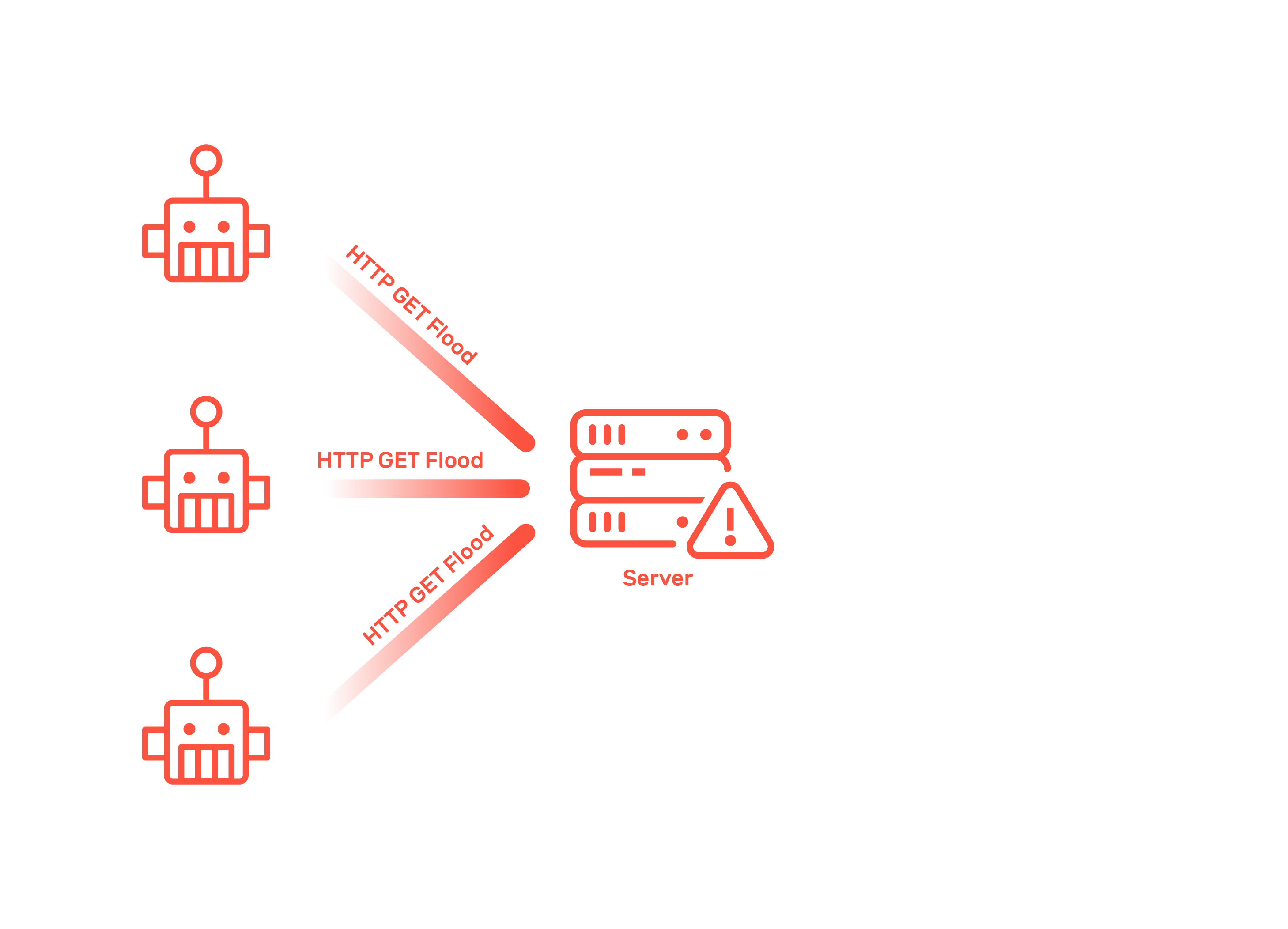
Complex Protection Against DDoS Attacks
Organizations often struggle to defend against sophisticated application-layer DDoS attacks that overload systems and disrupt critical services.

Business Disruptions Due to Downtime
DDoS attacks cause costly outages, damaging revenue and customer trust. Many companies lack scalable, redundant systems to ensure business continuity during attacks.

Complicated Implementation
Difficult setups and compatibility issues can cause delays and disrupt operations. Plus, additional hardware and software increase costs.

High Compliance Requirements
Meeting strict regulations like NIS-2, DORA, and GDPR is tough without certified solutions. Violations can result in legal and financial consequences for organizations.
Key Benefits of Myra's DDoS Protection

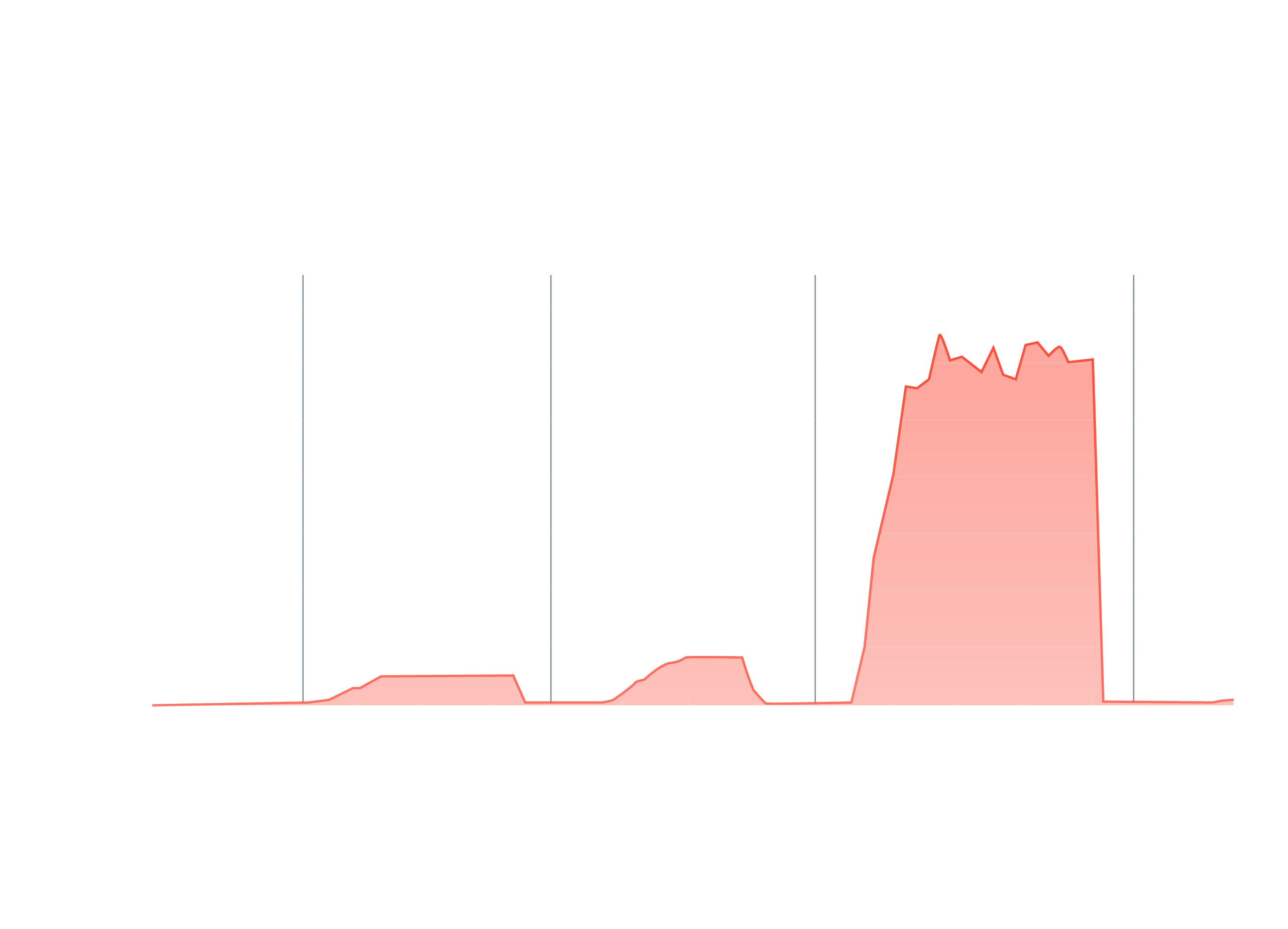
Stop DDoS Attacks in Real-Time
The AI-powered Myra protection processes hundreds of millions of HTTP requests per second and automatically mitigates attacks against web applications.

Keep Your Business Online at All Times
99.999 % SLA for service availability guaranteed. Prevent costly outages with Myra’s scalable, redundant DDoS mitigation solution.

Save Valuable Time and Resources
Get started right away with no extra hardware and software or complicated setups. Myra DDoS Protection works seamlessly with your existing infrastructure.

Ensure Full Compliance with Key Regulations
Myra itself is NIS-2-, DORA-, and GDPR-compliant and can help you meet regulatory requirements, especially in highly regulated sectors.
Certified Security You Can Rely On
All DDoS Protection Features

Advanced GeoIP Blocking
Myra DDoS Protection can block suspicious clients based on GeoIP information like region, country, or other IP characteristics.

Rate Limiting
Determine the number of web requests conspicuous IP addresses are allowed to make within a specified period.

Automatic Notification
In the event of an attack, have Myra automatically inform you based on your predefined escalation and notification levels.

Detailed Reporting
After the DDoS mitigation, receive individual reporting on the duration, type, and strength of the attack.

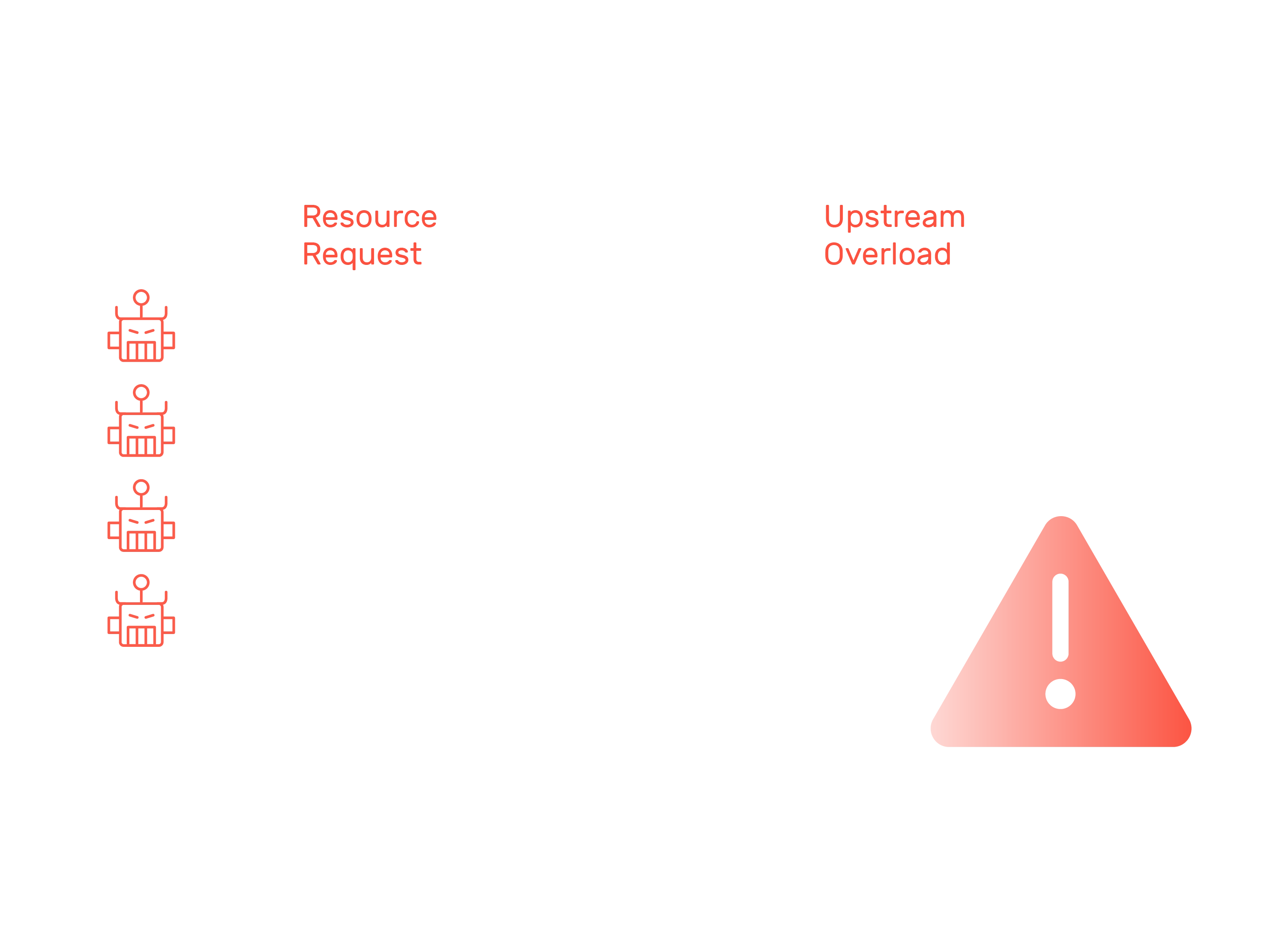
Upstream Monitoring
Myra monitors your upstream 24/7 and automatically notifies you of any communication issues with the origin server.

Certificate Management
Issue automated SSL/TLS certificates and keep track of everything with a centralized management system.

SSL/TLS Cipher Management
Enjoy the benefits of a continuously updated SSL/TLS configuration based on the latest security standards.

Broad Technology Support
Get seamless integration with Myra. We support modern web technologies such as HTTP/2, WebP, ChaCha20, WebSocket, and WebRTC.

Rely on IPsec
Get the encrypted forwarding of clean traffic for increased security requirements with this optional Myra feature.
How It Works
The Setup
Step 1
Upload Your TLS Certificates
Allow Myra to terminate the TLS connection and inspect traffic at a deep packet level by uploading your certificates through either:
The Myra API for automated integration.
The Myra App (WebGUI) for a user-friendly manual setup.
Step 2
Configure your Security Filters
Myra's SOC collaborates with you to customize the DDoS Protection settings:
Set up multi-layer filtering rules to block malicious traffic.
Implement customized security filters for granular traffic control.
Test your configuration (using Myra DNS explicitly).
Step 3
Adjust your DNS Settings
There are multiple ways to use the Myra DNS as the default DNS server:
Stay with your current authoritative DNS server. In this case, you have two alternative options:
Adjust your A or AAAA record to Myra's IP address.
Point your CNAME record to Myra.
Transfer your authoritative DNS server to Myra by importing existing zones.
The Mitigation
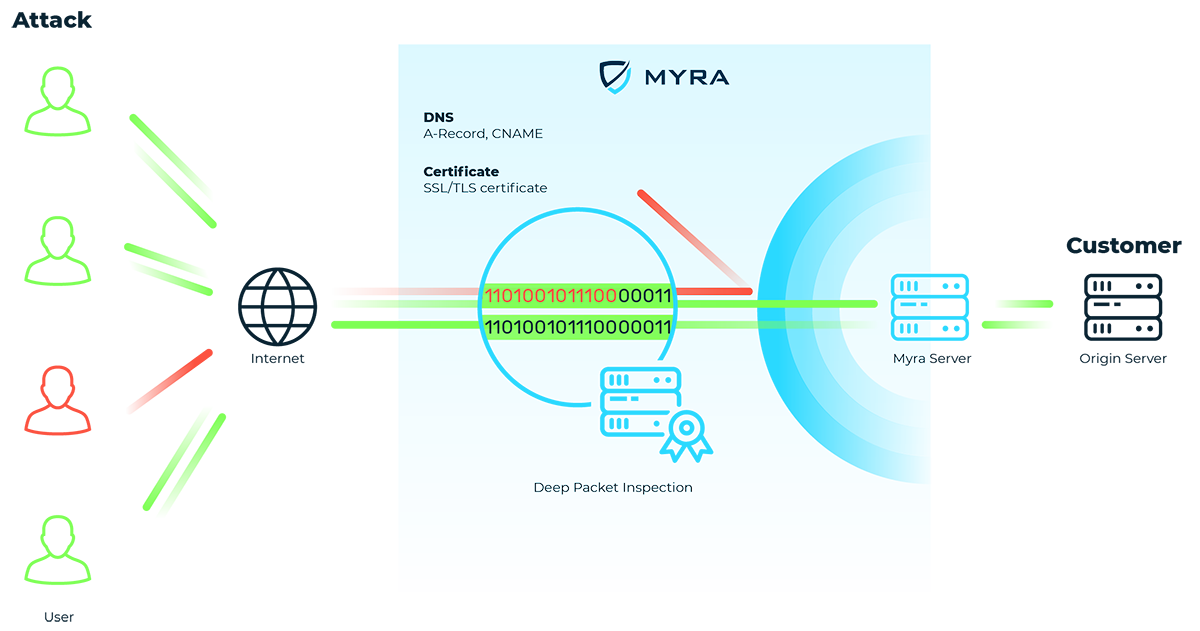
Malicious traffic flows are blocked by multi-level filter layers. Valid requests, on the other hand, continue to reach your infrastructure as usual via a redundant HTTP/S reverse proxy.

Malicious traffic flows are blocked by multi-level filter layers. Valid requests, on the other hand, continue to reach your infrastructure as usual via a redundant HTTP/S reverse proxy.
Anti-DDoS Spotlight
Myra DDoS Protection defends you against these and many other threats:
Protect Your Business from DDoS Threats Today
Get a Customized Solution That Fits Your Needs.
Myra's automated defenses take effect in less than a second.

Service level agreement (SLA) for availability of up to 99.999%.

Myra can defend against so-called extreme DDoS attacks with up to 1 Tbps, 250 million PPS, 5 million TPS, and far more than the required 50,000 bots.

Over 500 companies from highly regulated sectors such as finance, government institutions, healthcare, and critical infrastructure place their trust in us.
"Myra puts us in a solid position in terms of cybersecurity, web-performance and compliance."
– Hendrik Hoffmann, Division Manager Technology at Sparkassen-Finanzportal GmbH

Frequently asked questions about DDoS protection
DDoS protection (also known as anti-DDoS) refers to systems for defending against or mitigating cyberattacks by means of distributed denial of service. DDoS aims to cause delays and outages of websites and IT infrastructures via artificial requests. DDoS protection solutions are available either as a hardware appliance for implementation in your own data center or as a security-as-a-service solution via the cloud. Cloud-based DDoS protection can be used without additional hardware or software and therefore requires less effort to implement. The IT security provider takes care of the configuration and operation of the DDoS protection. DDoS protection as a hardware appliance, on the other hand, requires a high level of expertise to efficiently implement and configure the protection solution in your own data center. On-premises services, where the DDoS protection is installed and operated by the protection service provider itself in the customer's data center, are a middle ground.
Myra is regularly audited. These independent tests confirm Myra's ability to fend off so-called extreme DDoS attacks (DRS score 6) with up to 1 Tbps, 250 million PPS, 5 million TPS and much more than the required 50,000 bots.
The cost of DDoS protection varies depending on the desired deployment model (cloud, hardware or on-premises) and the required traffic bandwidth and number of domains to be protected. As a rule, security-as-a-service models as an anti-DDoS solution are cheaper for most companies than the in-house variant in their own data center. Full-service operators take on the initial implementation, continuous operation and configuration adjustments of security systems. Continuous monitoring of the secured systems is also included in order to ward off attacks as quickly as possible. The recruitment of cyber security experts in particular is a major obstacle and often significantly slows down the commissioning of hardware appliances. According to Bitkom, there are 137,000 vacancies for IT experts across all sectors in Germany (as of Nov. 2022). On average, it takes seven months to find suitable candidates for vacancies.
DDoS protection for dedicated protection against attacks on the application layer (layer 7) relies on multi-layer granular filtering methods that include fingerprinting, blocklisting and request limiting. This enables DDoS protection to effectively identify and fend off harmful traffic in the shortest possible time. In contrast to attacks on layer 3/4, attacks on layer 7 are based on already established connections of services and protocols such as HTTP, HTTPS, FTP or SMTP. For this reason, such attacks are very difficult to distinguish from regular traffic using conventional anti-DDoS solutions, such as those supplied as standard by most hosters. Without dedicated DDoS protection to defend against layer 7 attacks, the targeted systems are at acute risk of failure.
Protection solutions for defending against distributed denial of service (DDoS) attacks also protect against denial of service (DoS) attacks, as the attacks use the same methods. In both cases, malicious traffic is directed to a web resource via an attack tool with the aim of overloading the affected web servers. However, while in a DoS attack the attack originates from a single system, cyber criminals use distributed botnets consisting of hundreds or thousands of systems for DDoS attacks. As such botnets are becoming increasingly easy for criminals to access via illegal marketplaces on the darknet, the more powerful DDoS attacks are increasingly replacing conventional DoS attacks. On the part of the affected organizations, this trend makes anti-DDoS defense immensely more difficult – dedicated protection solutions as DoS/DDoS protection are therefore a prerequisite for successful defense.