New: Flexible service plans for Myra WAF. Learn more!
Home>
Multi-factor authentication
At one look
- 01. A definition of multi-factor authentication
- 02. How does multi-factor authentication work with banks?
- 03. How does multi-factor authentication work with online services?
- 04. Against which threats does multi-factor authentication provide protection?
- 05. How do I set up multi-factor authentication?
- 06. Why do I need a recovery code?
- 07. How does an authentication app work?
- 08. How secure are the different authentication methods?
- 09. How do I disable multi-factor authentication?
- 10. Myra supports multi-factor authentication
- 11. What you need to know about multi-factor authentication
01
A definition of multi-factor authentication
Multi-factor authentication provides significantly greater security than the use of passwords alone. By combining several independent factors, the identity of a user is verified beyond doubt. Factors can be divided into three groups: something that only the user knows, possesses, or is inseparable from. Specific examples are a password, a hardware security token in the form of a USB stick or smartphone, and biometric features such as the user’s face or fingerprint.
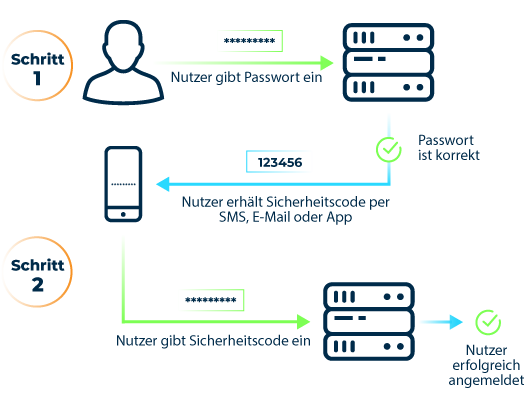
Only when the user specifies factors from at least two different groups when logging in will he or she be granted access to his or her account. In most cases, a security code that is only valid for a short time is requested, which the user receives via text message, email, voice call, or smartphone app. Most online services now offer this type of two-factor authentication (2FA).
Procedures involving three or more factors are also used, particularly in professional environments. If login requires at least one item from each of the three groups, this is known as three-factor authentication (3FA). An example of this would be the combination of a password, device ID, and fingerprint. In four-factor authentication (4FA), the user’s location is frequently also checked, such as whether the user is logging on from the internal network.
If multi-factor authentication is enabled, an attacker will be unable to do something with the username and password alone because he lacks the MFA key, which is used as an additional factor to verify identity. For most services, however, users first have to set up multi-factor authentication in their account settings.
04
Against which threats does multi-factor authentication provide protection?
Login credentials can quickly end up in the wrong hands. For one, attackers take advantage of the ignorance and gullibility of many internet users to gain access to login information. Secondly, cybercriminals gain direct access to inadequately secured provider databases containing thousands or even millions of login credentials. On the Darknet, data like this, often originating from leaks or hacker attacks, is traded at bargain prices.
Multi-factor authentication protects an account even if the login credentials have been compromised. Attackers will still be unable to gain access to the account using the username and password alone because they do not have the MFA key as an additional factor for proof of identity. Accounts with multi-factor authentication enabled are therefore safe from the following threats:
Phishing
Phishing attacks are aimed at stealing valuable login credentials for things like online banking or payment services. To achieve this, phishers often send millions of spam emails that include links luring unsuspecting users to fake login pages. These login pages are typically indistinguishable from the original. When a user enters his or her login credentials, they are sent straight to the scammers.
Malware
The use of malware represents another method commonly employed by cybercriminals to get login credentials. They use spam emails or tampered websites to inject a keylogger into the system, for instance. This type of malware logs every user keystroke to sniff out login credentials.
Brute force
Cracking passwords by brute force has, for years, been part of the standard repertoire of hackers. This method of attack is used to crack secured accounts by repeatedly and systematically entering username/password combinations. Using automated tools and powerful hardware, simple login credentials can be “guessed” in a short time. However, the more complex passwords become, the more computing power and time are required in the brute-force method.
Credential cracking
In credential cracking, cybercriminals use leaked lists of usernames and passwords to gain access to an online account. If the attackers know the username for a particular account with a provider, but not the password, they use bots to test known passwords automatically. A single match will then give them full access to the account.
Credential stuffing
As with credential cracking, in credential stuffing, hackers take advantage of the convenience of many users who often use the same weak default password for a variety of accounts. Once attackers come into the possession of a leaked username/password combination, credential stuffing enables them to quickly identify active accounts. All they have to do is to start automated requests using the known login credentials, e.g., to webshops, online banks, and even corporate accounts. The bots used for this purpose are capable of testing millions of username/password combinations within hours. The criminals then sell any matches to active accounts or use them for more extensive attacks.
06
Why do I need a recovery code?
After setting up multi-factor authentication, it is recommended that you write down or print out one of the recovery codes provided and keep it in a safe place. This is the only way to ensure continued access to the account if there are any problems with the authenticator app or if the smartphone or USB security key gets lost. Note: Each recovery code can only be used once.
08
How secure are the different authentication methods?
In general, all methods employing multi-factor authentication provide significantly greater security than the use of passwords alone. If the device is free of malware, the use of an authentication app is considered to be more secure than receiving an MFA key via text message. This is because codes sent by text message can be intercepted or redirected by attackers with a bit of effort. For example, they use the victim’s name to contact their phone provider and pretend to have lost their cell phone and SIM card. They have a new card sent to them and have the old one blocked. If the phone provider’s security measures are inadequate, this is how attackers gain control over the victim’s phone number and all the online accounts linked to this number.
The greatest level of security is provided by multi-factor authentication employing hardware security tokens in the form of a USB stick or smart card. The user must connect it to a computer or hold it in front of a reader to log in. The token is uniquely identified and additional factors are requested for authentication, such as a fingerprint and a PIN. If the factors entered match the token, the user is granted access to his or her account. If the token is lost, the account remains protected against unauthorized access because the additional factors are still required.
10
Myra supports multi-factor authentication
If you want to protect your online accounts as effectively as possible, you should use multi-factor authentication in addition to complex passwords. Of course, Myra’s Security-as-a-Service platform also supports login via MFA: In the web application, customers can easily enable “Confirmation in two steps” under My Account > Security to easily comply with internal security requirements.
Want to learn more about our solutions, use cases and best practices for attack defense? In our download area you will find product sheets, fact sheets, white papers and case studies.
About the author
Stefan Bordel
Senior Editor
About the author
Stefan Bordel has been working as an editor and technical writer at Myra Security since 2020. In this role, he is responsible for creating and maintaining website content, reports, whitepapers, social media content and documentation. This role allows him to bring his extensive experience in IT journalism and technical knowledge to an innovative cyber security company. Stefan previously worked at Ebner Verlag (formerly Neue Mediengesellschaft Ulm) for 7 years and joined the online editorial team at com! professional after working for Telecom Handel. He gained his first journalistic experience during various internships, including at the IT website Chip Online. As a passionate Linux user, he follows the IT scene closely, both privately and professionally.