New: Flexible service plans for Myra WAF. Learn more!
Home>
Unauthorized Access
What you need to know about Unauthorized Access
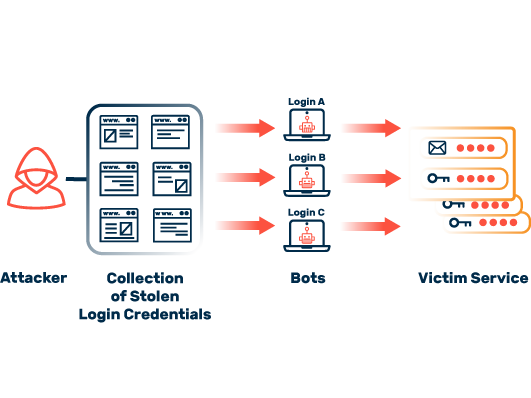
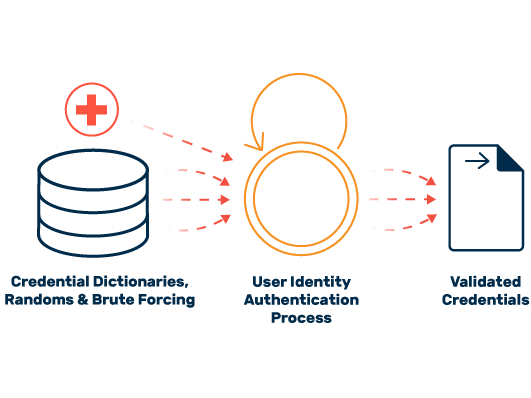
To obtain account credentials, attackers take advantage of the convenience of many users. Even today, a majority of Internet users use weak passwords, which are then also used multiple times across a variety of different services. Once such a password is known, for example as a result of a data breach, it is easy for cybercriminals to locate and compromise other accounts on the Internet with these access data.
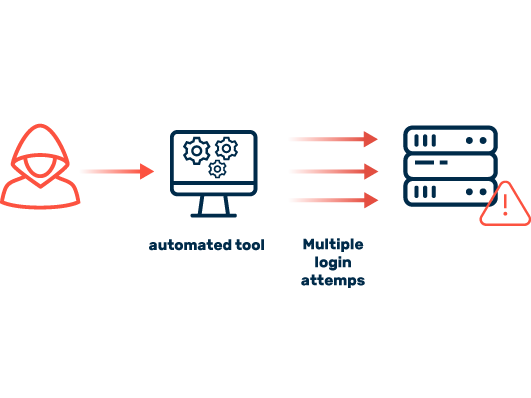
Attackers rely on automated tools to take over online accounts. These enable cybercriminals to check millions of accounts for possible vulnerabilities in a very short time and take over weakly secured accounts. Those affected often only find out about the takeover of their accounts when it is too late and abusive actions are carried out via the services.